You're viewing Apigee Edge documentation.
Go to the
Apigee X documentation. info
Attach the Monetization Limits Check policy to API proxies to enforce monetization limits. Specifically, the policy is triggered under the following conditions:
- Developer accessing monetized API is not registered or has not subscribed to the rate plan.
- Developer has exceeded the transaction volume for the subscribed rate plan.
- Developer pre-paid account balance or post-paid credit limit has been reached.
The Monetization Limits Check policy is designed to raise a fault and block an API call in situations like those listed above. The policy extends the Raise Fault policy (see Raise Fault policy), and you can customize the message returned. The applicable conditions are derived from business variables.
Attaching a Monetization Limits Check Policy using the UI
To enforce monetization limits, a Monetization Limits Check policy must be attached to the request flow in API proxies that access your APIs. The Monetization Limits Check policy should be attached after any VerifyAPIKey or AccessTokenValidation policy in the request.
You can attach a Monetization Limits Check policy when you create an API proxy or after an API proxy is created.
When you create an API proxy, as described in Build a simple API proxy, if monetization is installed, the Monetization configuration section appears in the wizard.
Edge
On the Common policies page of the wizard, select the Enforce monetization limits checkbox to attach a Monetization Limits Check policy.
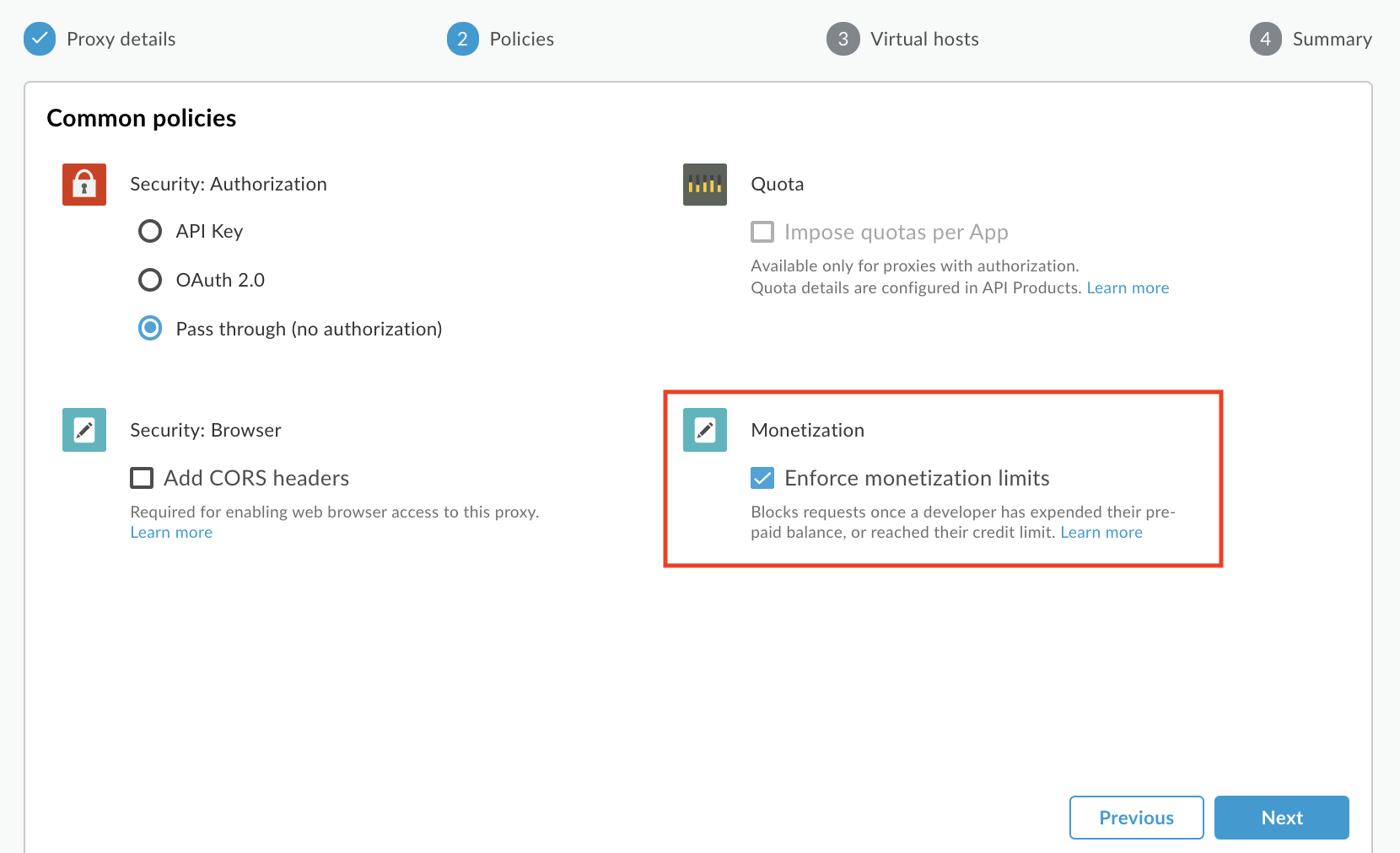
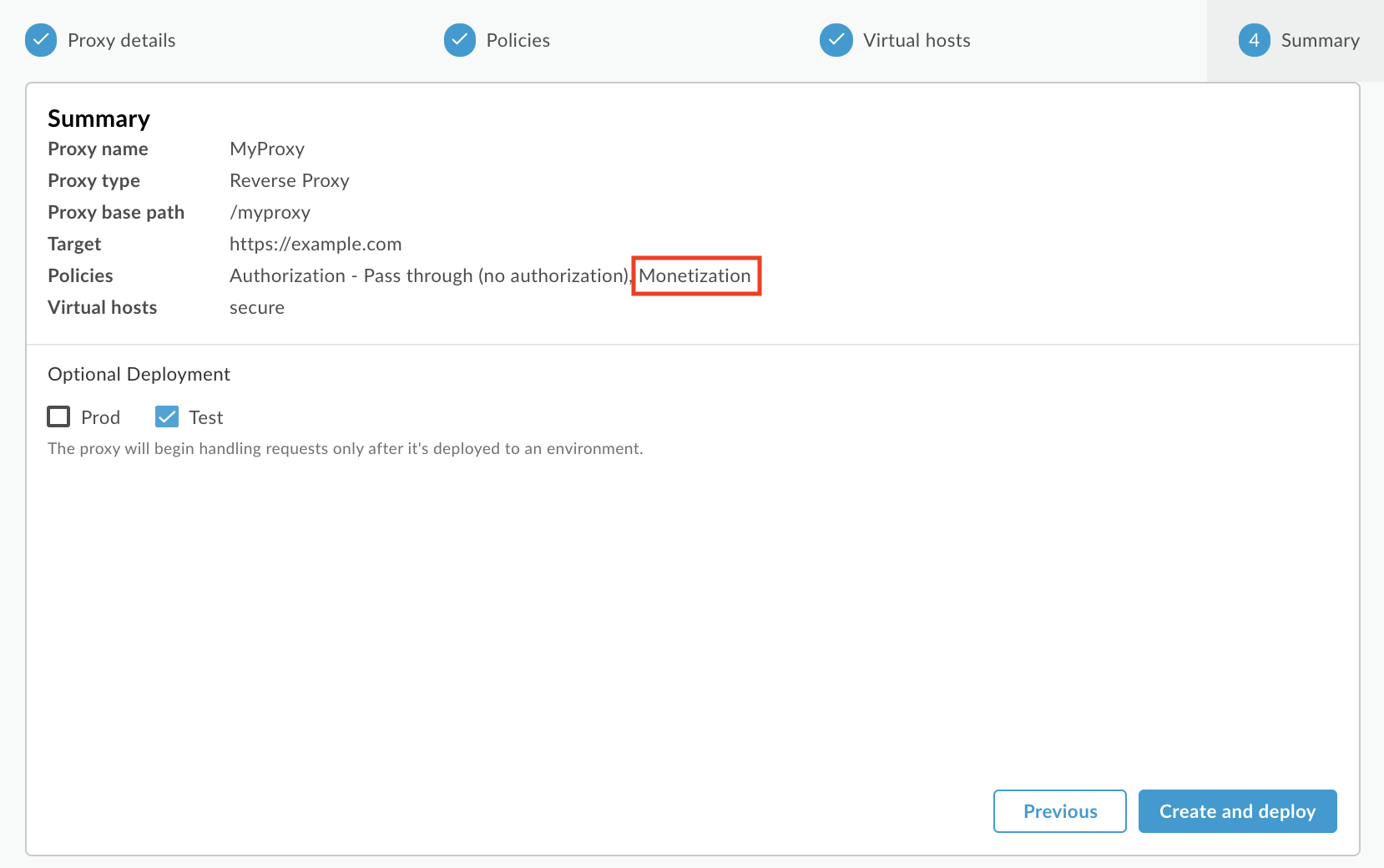
Note that on the Summary page of the wizard, the Policies are summarized. Ensure that the Monetization policy is listed, indicating that the Monetization Limits Check policy will be attached to the API proxy, as described below.
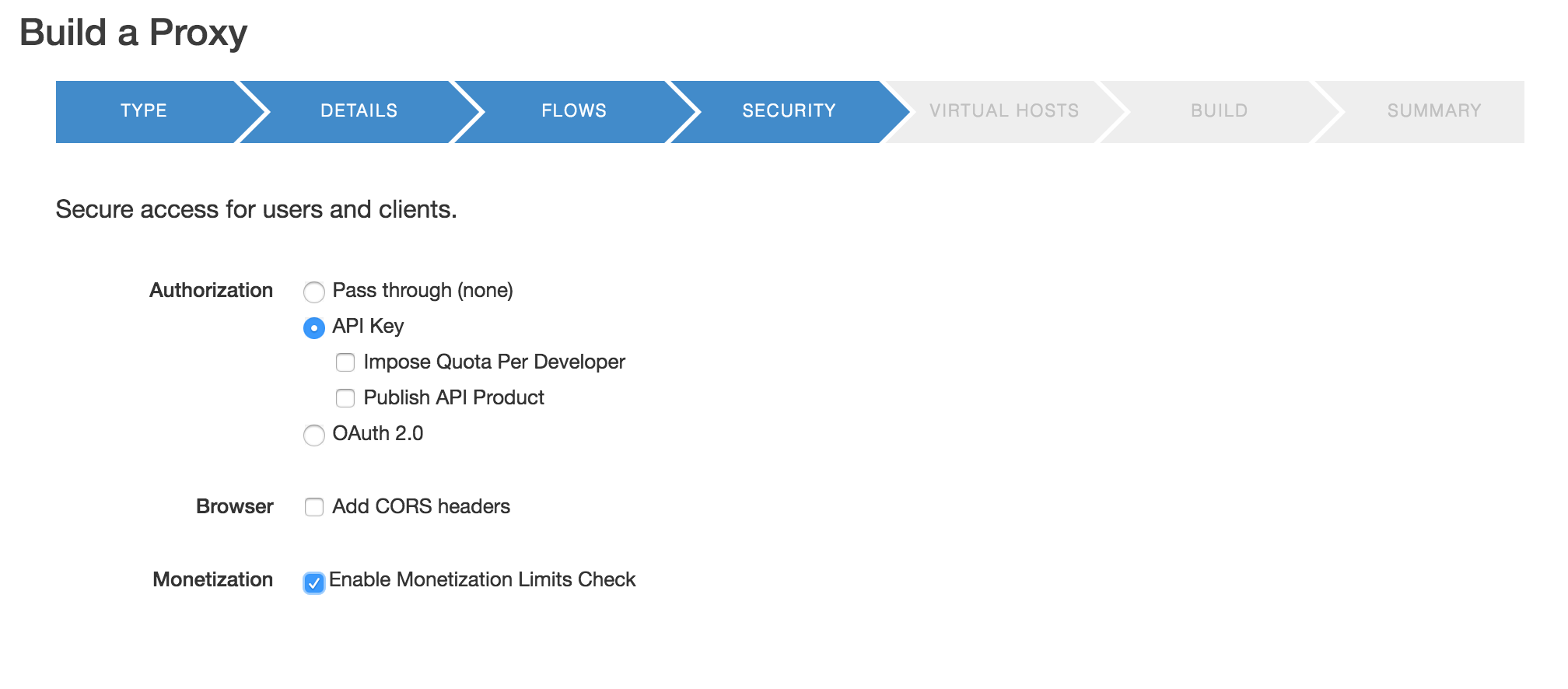
Classic Edge (Private Cloud)
On the Security page of the wizard, select the Enable Monetization Limits Check checkbox to attach a Monetization Limits Check policy.
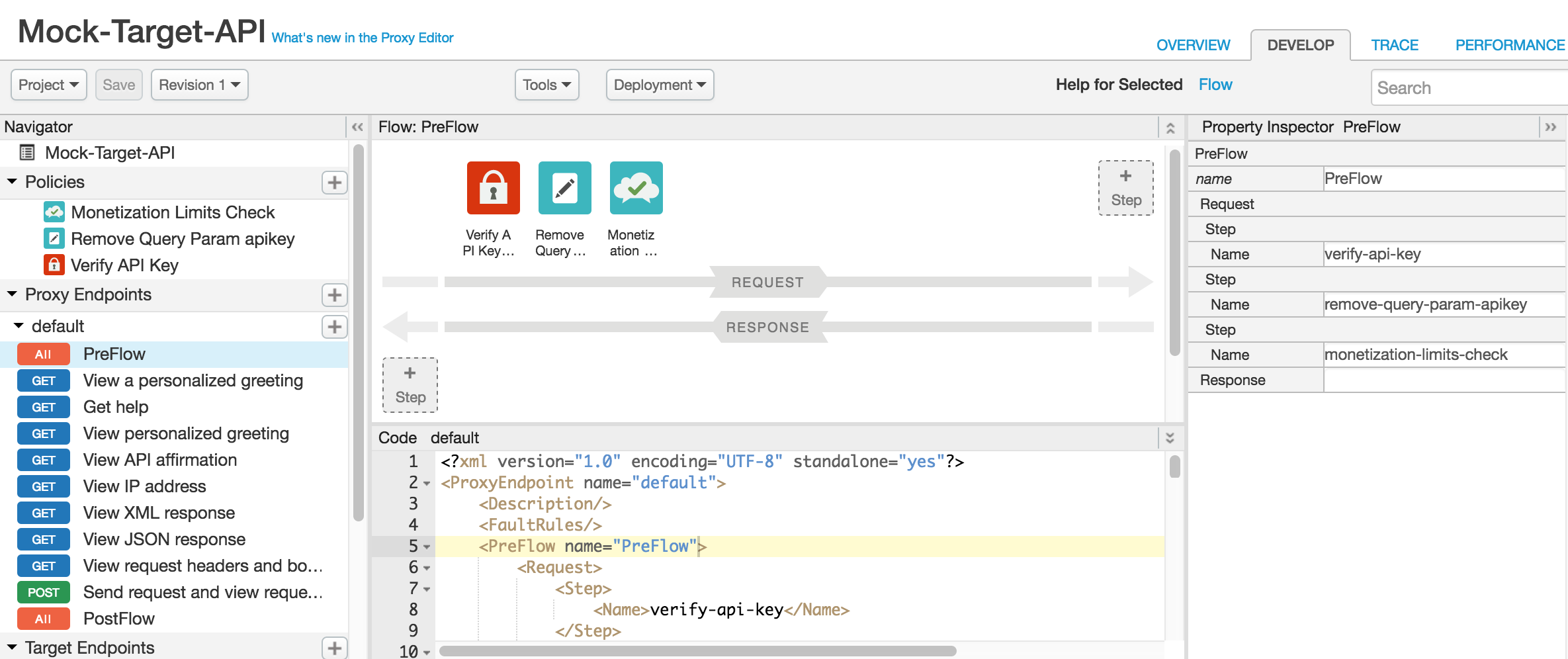
The Monetization Limits Check policy is added to the ProxyEndpoint request PreFlow, after the VerifyAPI Key or AccessTokenValidation policy, as show in the following figure.
To add the Monetization Limits Check policy to an API proxy that has already been created:
- In the API Proxy Editor, click PreFlow for the default proxy endpoint.
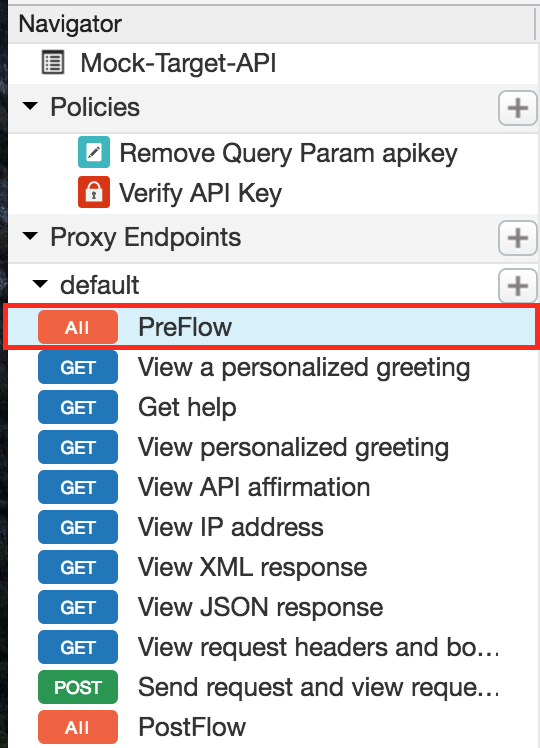
- In the Request flow, click +Step.
- Select Monetization Limits Check in the Mediation category.
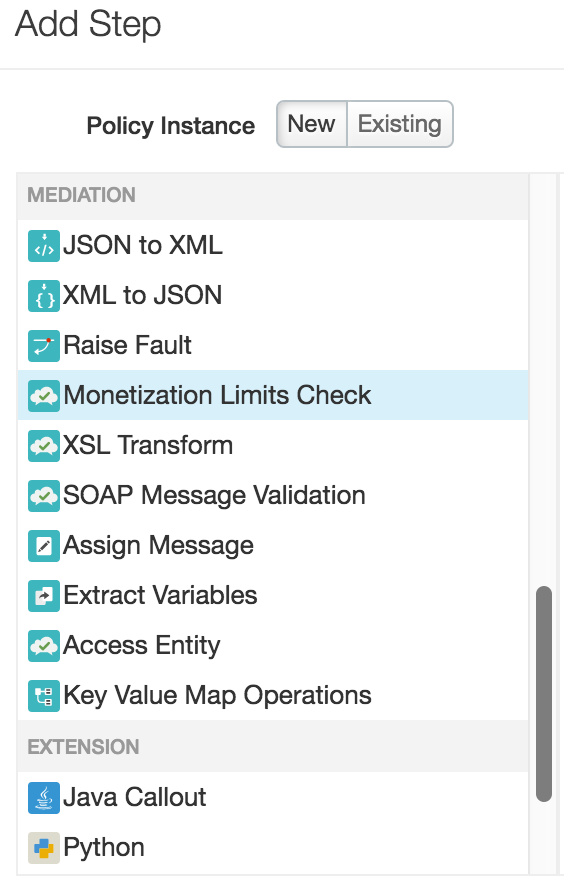
- Modify the fields in the Add Step dialog, as desired, and click Add.
The policy is attached to the request flow after any VerifyAPI Key or AccessTokenValidation policy, and will be enforced on request messages from client apps to the ProxyEndpoint PreFlow.
For more information about configuring the MonetizationLimitsCheck policy XML file, see MonetizationLimitsCheck policy.
