You're viewing Apigee Edge documentation.
Go to the
Apigee X documentation. info
What you'll learn
Through this tutorial, you'll learn to:
- Add a policy that affects the request and response.
- See the effects of the policy.
What you'll need
- At least one policy in your proxy (also part of the Get Started tutorial).
curlinstalled on your machine to make API calls from the command line.
Add the Spike Arrest policy
In this tutorial, you'll add and configure the SpikeArrest policy to guard the target service against sudden traffic spikes that can be caused by an increase in usage, buggy clients, or malicious attacks. When the number of requests exceeds the rate limit, the API returns an HTTP 500 error for a request.
Add the Spike Arrest policy to an API proxy:
- Sign in to apigee.com/edge.
- Select Develop > API Proxies in the left navigation bar.
- Select the API proxy to which you want to add the Spike Arrest policy.
If you followed the Get Started tutorial, you can add it to the "getstarted" proxy you created in Create an API proxy.
- In the editor for the new API proxy, click the Develop tab:
The API Proxy Editor lets you see the structure of your API proxy and configure its flow. The editor presents a visual representation of your proxy's request and response message flow as well as an editable display of the underlying XML that defines the proxy.
- In the left Navigator pane, click PreFlow under Proxy Endpoints > default. (Other tutorials will cover the concept of flows.)
- Click the top +Step button, corresponding to the Request PreFlow. This
displays a categorized list of all the policies you can create.
- Select Spike Arrest in the Traffic Management category. The New Policy
dialog appears:
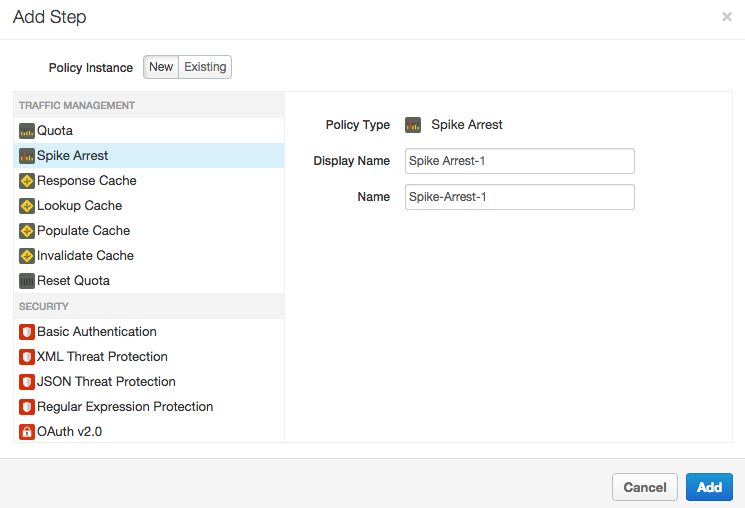
- Leave the default names, and click Add. The new policy is attached to the PreFlow flow of a request.
- In the Navigator, ensure that PreFlow under Proxy Endpoints
> default is still selected and note the following in the API Proxy Editor:
- The new Spike Arrest-1 policy is added under Policies in the Navigator in the left side of the API Proxy Editor.
- The Spike Arrest-1 icon is added to the Designer view in the top center of the API Proxy Editor, which is a visual representation of your proxy's message flows.
- The XML for the policy is displayed in the Code view in the bottom center of the API Proxy Editor.
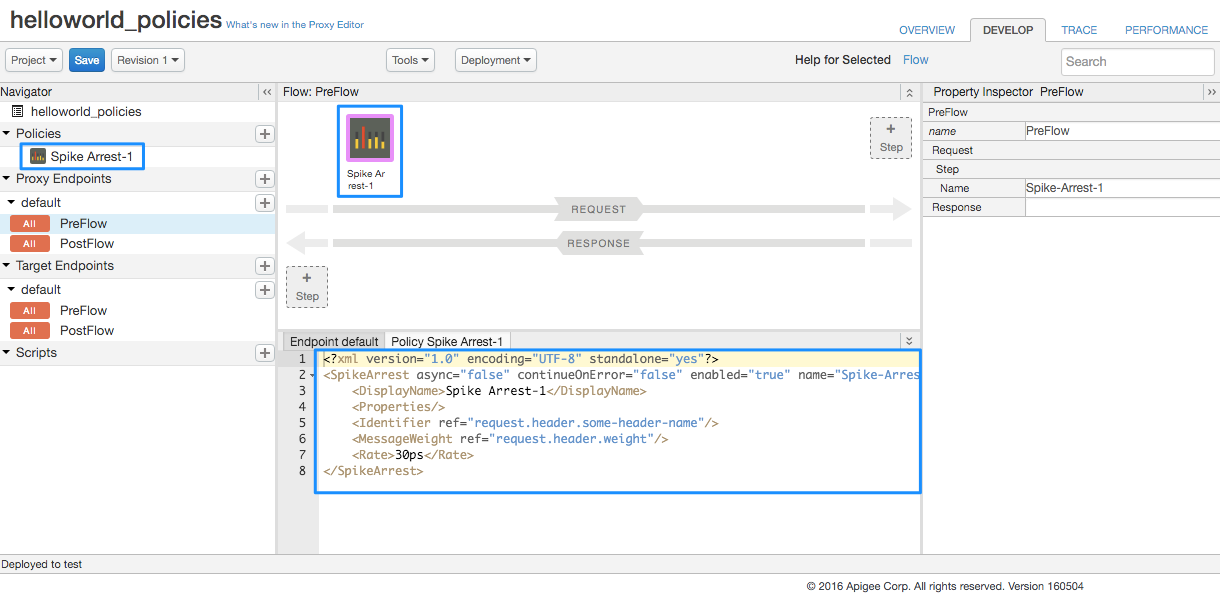
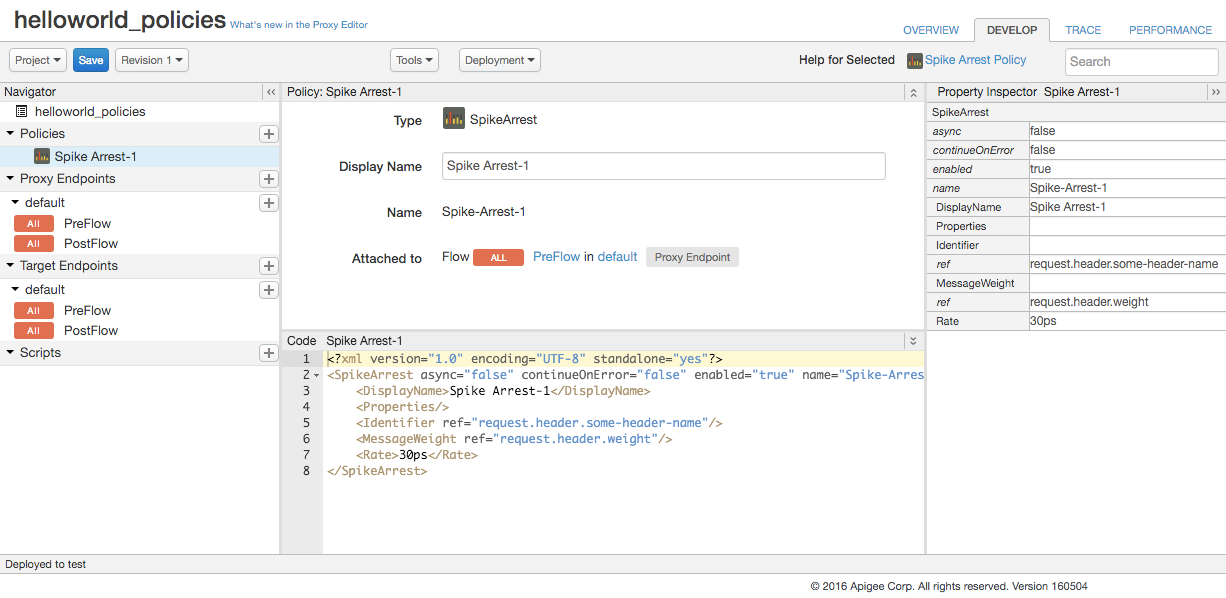
- In the Navigator, select Spike Arrest-1 under Policies and note the
following in the API Proxy Editor:
- The policy details are displayed in the Designer view in the top center of the API Proxy Editor.
- The XML for the policy is displayed in the Code view in the bottom center of the API Proxy Editor.
- The XML element and attribute values for the policy are displayed in the Property Inspector in the right side of the API Proxy Editor.
-
In the XML for the policy, change the value of the
<Rate>element to 1pm (which translates into roughly 2 requests allowed every 60 seconds in the cloud).You can specify the rate as an integer value per minute (
pm) or per second (ps). This is a very low limit and is used only for this tutorial to demonstrate the policy. Typically, you set it to a much higher limit.Notice that the
Ratevalue in the Property Inspector also changes to "1pm". Alternatively, you can change the Rate value in the Property Inspector and it will be reflected in the XML view. - Click Save to save the current revision with your changes.
-
Call the API using
curl, substituting your Apigee organization name for org_name:curl "http://org_name-test.apigee.net/getstarted"
For example:
curl "http://ahamilton-eval-test.apigee.net/getstarted" | python -m json.tool
Make sure the request succeeds and you see the same XML response as you did previously. (You can also enter just the URL in a web browser.)
- Execute the
curlcommand (or refresh the browser window) two or three more times within one minute, and notice that you get the following message because you exceeded the rate limit of the policy:{ "fault": { "faultstring":"Spike arrest violation. Allowed rate : 1pm", "detail": { "errorcode":"policies.ratelimit.SpikeArrestViolation"} } }If you try making more calls within a minute, you should continue to get the fault message.
- Edit your policy to set the <
Rate>limit to 15pm (which translates into roughly 2 calls allowed every 4 seconds in the cloud), and then save the API proxy. - Execute the
curlcommand or refresh the browser repeatedly (curlis faster). Notice that if you make one or two calls within 4-second intervals, your calls succeed. If you make the calls quickly, more than two in within 4 seconds, you should get the fault. But after each 4-second interval you can continue making calls, as opposed to being blocked out for an entire minute (with the 1pm setting).
