You're viewing Apigee Edge documentation.
Go to the
Apigee X documentation. info
Apigee Sense protects your APIs from unwanted request traffic, analyzing API request traffic and identifying patterns that might represent unwanted requests. Apigee Sense protection rules only prevent attacks that are made specifically targeted towards API proxies. Apigee Sense does not prevent DDoS attacks. If DDoS attack prevention is required, a WAF, such as Google Cloud Armor should be used in front of Apigee.
For an explanation of the level of support Apigee provides for protecting against DDoS attacks, see DDoS defense in Edge.
Using the Apigee Sense analysis, you can identify clients making unwanted requests, then take action to allow, block, or flag those requests.
With Apigee Sense, you can protect your APIs from request patterns that include:
- Automated behavior that blends with human behavior
- Persistent attempts from the same IP
- Unusual error rates
- Suspicious client requests
- Data crawling
- Key harvesting
- Activity bursts
- Geographical patterns
Detecting unwanted requests
Behind the scenes, Apigee Sense does its detecting from your request metadata, then provides its analysis results for you to review. You can review the analysis results in the Apigee Sense console. When a pattern looks suspicious, you can take a closer look at details behind it to decide whether to take action.
To detect request patterns, Apigee Sense stores and analyzes request metadata. As clients make requests, Apigee Sense collects request metadata, then analyzes that data in batches to look for patterns.
See Getting started with the Apigee Sense Console.
Patterns discovered
You can view the results of analysis in the Apigee Sense console as patterns. Each pattern represents a set of request characteristics found during analysis.
Here are a few pattern examples:
- Reasons. You can view requests to your API filtered through many built-in configurations called reasons. A reason represents a set of criteria and thresholds that might indicate suspicious activity. For example, "content robber" describes requests with few OAuth sessions and a large volume of traffic in a 5-minute window. It has thresholds for numbers of calls from an IP, percent total traffic, and unique sessions.
- Geography. You view requests filtered by their geographic origin.
- AS Organization. You can view requests filtered by the autonomous system organization they came from.
In the following illustration, the Apigee Sense console lists reason patterns discovered during analysis of request metadata.
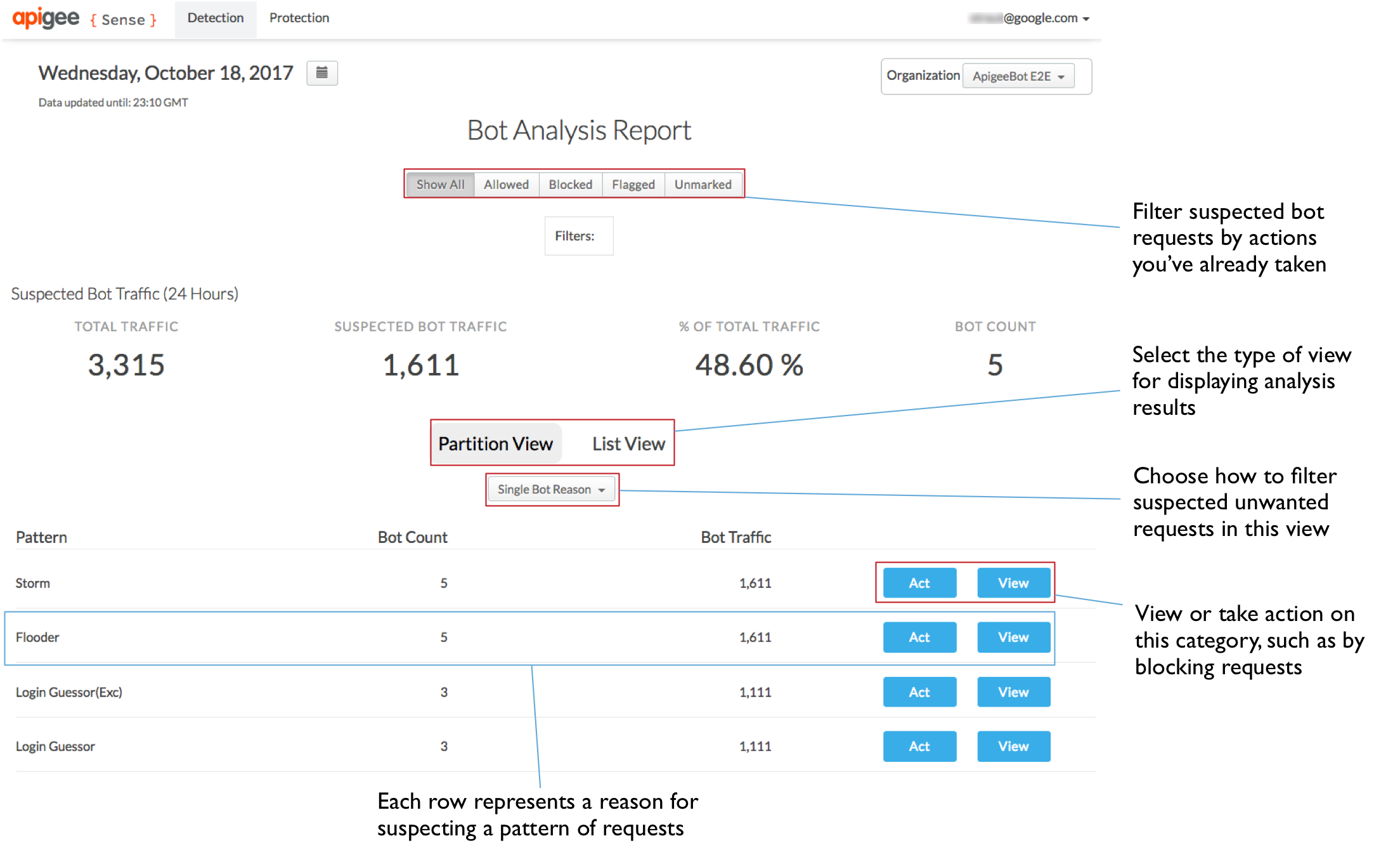
For more detail on patterns, particularly reasons, see Taking action on suspicious activity.
Data analyzed
Apigee Sense collects request metadata to analyze your API traffic. The following lists the kinds of metadata analyzed, along with a few of the questions Apigee Sense looks at in order to discover patterns.
- Client characteristics. What is their IP address and geographical location? What user agent and family was used? What device?
- Target characteristics. URIs targeted by clients. Are they repeatedly hitting a login proxy?
- Request characteristics. Which HTTP verb and request URI was used? What was the path suffix?
- Response characteristics. What response code did the client receive? Was it an error? How large was the response?
- Timing and quantity. Did a request spike occur in a short period? When was it? How big was the spike? Where were the requests coming from?
You can use the Detailed View to drill down on request characteristics when determining whether a client's requests are unwanted.
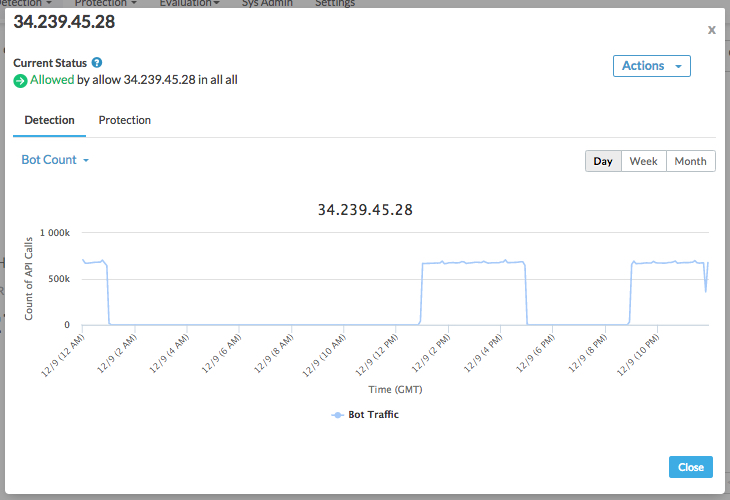
For more on looking at analysis details, see Getting started with the Apigee Sense Console.
Protecting your APIs
Using analysis results from Apigee Sense, you make your own decisions about whether a client or set of requests merits action.
In the Apigee Sense console, you can view traffic details for a particular IP address (or group of addresses). When you identify an unwanted client, you can take action, such as to block the client's requests.
Available actions
Using the Apigee Sense console, you can take the following actions for an IP address that you've decided is unwelcome.
| Action | Description |
|---|---|
| Block | Blocks requests coming from a specified IP address, returning a 403 response to the client. Blocked requests don't reach your proxies. |
| Flag | Add a special HTTP header that your proxy can look for. Apigee Edge will add an X-SENSE-BOT-DETECTED header with a value of SENSE. |
| Allow | Allows the request to proceed to your proxies. |
For more about taking action on suspicious requests, see Getting started with the Apigee Sense Console.
Overview of Apigee Sense
Apigee Sense uses adaptive algorithms that are tuned with data from across multiple datasets. As a result, it is able to distinguish legitimate traffic more effectively than would be possible from a single source of data. Adaptive algorithms automate the identification and tracking process. As a result, you need only to decide how to deal with suspicious traffic from a IP address.
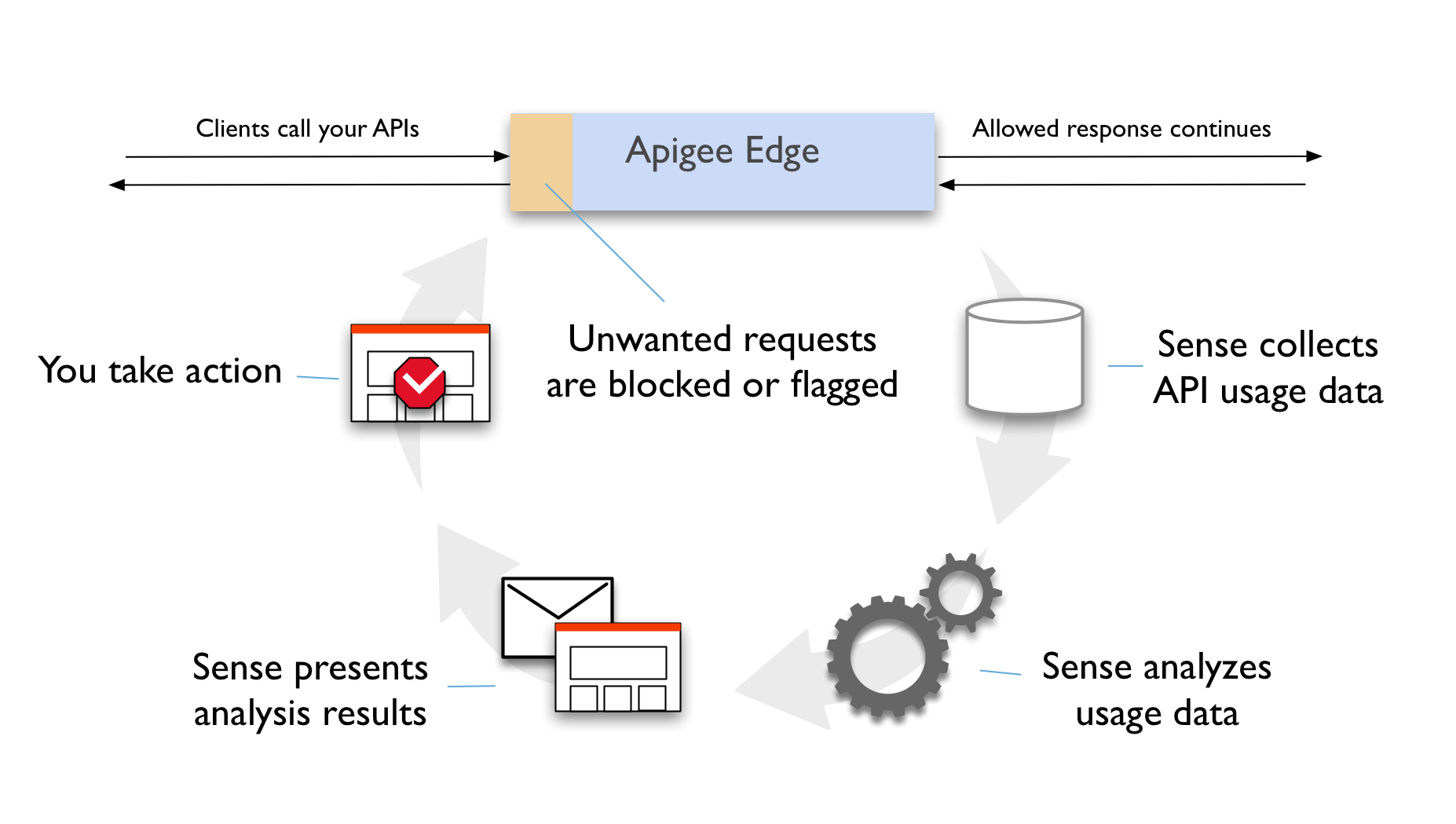
Apigee Sense is made up of four components:
- A collection engine collects a large number of relevant signals as traffic passes through Apigee Edge. Apigee Sense collects typical metadata about the source and target for the API call, as well as and metadata relating to both request content and response status. It also collects timing and latency information.
- The analysis engine assembles all the collected data into a summary data structure. Apigee Sense does a deeper analysis on this structure, examining how each request source behaves. Apigee Sense then makes judgements on whether the source has a suspicious signature.
- Through the curation engine, Apigee Sense presents analysis results to users. With these results, you can specify the action to take for each identified suspicious client.
- Finally, the action engine identifies requests as originating from suspicious clients in real time and takes the appropriate action required on such traffic.
