Per impostazione predefinita, accedi Nuova UI Edge su HTTP utilizzando l'indirizzo IP o il nome DNS del nodo Edge UI e la porta 3001. Ad esempio:
http://newue_IP:3001
In alternativa, puoi configurare l'accesso TLS alla UI Edge in modo che puoi accedervi nel modulo:
https://newue_IP:3001
Requisiti TLS
La UI Edge supporta solo TLS v1.2. Se abiliti TLS nell'UI Edge, gli utenti devono connettersi alla UI Edge utilizzando un browser compatibile con TLS v1.2.
Proprietà di configurazione TLS
Esegui questo comando per configurare il protocollo TLS per la UI Edge:
/opt/apigee/apigee-service/bin/apigee-service edge-management-ui configure-ssl -f configFile
Dove configFile è il file di configurazione che hai utilizzato per installare UI Edge.
Prima di eseguire questo comando, devi modificare il file di configurazione per impostare le proprietà necessarie che controllano TLS. Nella tabella seguente vengono descritti i che utilizzi per configurare il protocollo TLS per la UI Edge:
| Proprietà | Descrizione | Obbligatorio? |
|---|---|---|
MANAGEMENT_UI_SCHEME
|
Imposta il protocollo "http" o "https", utilizzato per accedere alla UI Edge. Il valore predefinito è "http". Impostala su "https" per abilitare TLS: MANAGEMENT_UI_SCHEME=https |
Sì |
MANAGEMENT_UI_TLS_OFFLOAD
|
Se "n", specifica che le richieste TLS alla UI perimetrale vengono terminate
dell'interfaccia utente Edge. Devi impostare Se "y", specifica che le richieste TLS alla UI perimetrale vengono terminate tramite un bilanciatore del carico, che inoltra quindi la richiesta alla UI perimetrale tramite HTTP. Se disabiliti TLS sul bilanciatore del carico, la UI perimetrale deve comunque tieni presente che la richiesta originale è stata inviata tramite TLS. Ad esempio, per alcuni cookie è impostato un flag di sicurezza. Devi impostare MANAGEMENT_UI_SCHEME=https MANAGEMENT_UI_TLS_OFFLOAD=y |
Sì |
MANAGEMENT_UI_TLS_KEY_FILE
|
Se MANAGEMENT_UI_TLS_OFFLOAD=n, specifica il percorso assoluto
ai file della chiave e del certificato TLS. I file devono essere formattati come file PEM con
nessuna passphrase e deve essere di proprietà di "apigee" utente.
Il percorso consigliato per questi file è:
/opt/apigee/customer/application/edge-management-ui Se la directory non esiste, creala. Se |
Sì se MANAGEMENT_UI_TLS_OFFLOAD=n
|
MANAGEMENT_UI_PUBLIC_URIS
|
Se Imposta questa proprietà in base ad altre proprietà nel file di configurazione. Ad esempio: MANAGEMENT_UI_PUBLIC_URIS=$MANAGEMENT_UI_SCHEME://$MANAGEMENT_UI_IP:$MANAGEMENT_UI_PORT Dove:
Consulta Installare la nuova UI Edge per ulteriori informazioni su queste proprietà. Se
|
Sì |
MANAGEMENT_UI_TLS_ALLOWED_CIPHERS
|
Definisce l'elenco di crittografie TLS disponibili come stringa separata da virgole o spazi. Stringa separata da virgole: MANAGEMENT_UI_TLS_ALLOWED_CIPHERS=TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 Stringa separata da spazi racchiusa tra virgolette doppie:
MANAGEMENT_UI_TLS_ALLOWED_CIPHERS="TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256" |
|
SHOEHORN_SCHEME
|
Prima di installare la nuova UI Edge, devi prima installare la UI Edge di base, chiamata shoehorn. Il file di configurazione dell'installazione utilizza la seguente proprietà per specificare il protocollo, "http", utilizzato per accedere alla UI Edge di base: SHOEHORN_SCHEME=http La UI Edge di base non supporta TLS, quindi anche se abiliti TLS nell'UI Edge, questa proprietà deve essere comunque impostata su "http". |
Sì e imposta su "http" |
Configura TLS
Per configurare l'accesso TLS alla UI Edge:
Genera il certificato e la chiave TLS come file PEM senza passphrase. Ad esempio:
mykey.pem mycert.pem
Esistono molti modi per generare un certificato e una chiave TLS. Ad esempio, puoi eseguire questo per generare un certificato e una chiave non firmati:
openssl req -x509 -newkey rsa:4096 -keyout mykey.pem -out mycert.pem -days 365 -nodes -subj '/CN=localhost'
- Copia i file della chiave e del certificato nella directory
/opt/apigee/customer/application/edge-management-ui. Se la directory non esiste, creala. Assicurati che il certificato e la chiave siano di proprietà di "apigee" utente:
chown apigee:apigee /opt/apigee/customer/application/edge-management-ui/*.pem
Modifica il file di configurazione che hai utilizzato per installare la UI Edge in imposta le seguenti proprietà TLS:
# Set to https to enable TLS. MANAGEMENT_UI_SCHEME=https # Do NOT terminate TLS on a load balancer. MANAGEMENT_UI_TLS_OFFLOAD=n # Specify the key and cert. MANAGEMENT_UI_TLS_KEY_FILE=/opt/apigee/customer/application/edge-management-ui/mykey.pem MANAGEMENT_UI_TLS_CERT_FILE=/opt/apigee/customer/application/edge-management-ui/mycert.pem # Leave these properties set to the same values as when you installed the Edge UI: MANAGEMENT_UI_PUBLIC_URIS=$MANAGEMENT_UI_SCHEME://$MANAGEMENT_UI_IP:$MANAGEMENT_UI_PORT SHOEHORN_SCHEME=http
Esegui questo comando per configurare TLS:
/opt/apigee/apigee-service/bin/apigee-service edge-management-ui configure-ssl -f configFile
Dove configFile è il nome del file di configurazione.
Lo script riavvia la UI Edge.
Esegui questi comandi per configurare e riavviare shoehorn:
/opt/apigee/apigee-service/bin/apigee-service edge-ui setup -f configFile
/opt/apigee/apigee-service/bin/apigee-service edge-ui restartDopo il riavvio, la UI Edge supporta l'accesso tramite HTTPS. Se non riesci ad accedere alla UI Edge dopo aver abilitato TLS, cancella il cache del browser e riprova ad accedere.
Configura la UI Edge quando TLS termina sul bilanciatore del carico
Se hai un bilanciatore del carico che inoltra le richieste alla UI Edge, potresti scegliere di terminare la connessione TLS sul bilanciatore del carico e quindi il bilanciatore del carico inoltra le richieste alla UI perimetrale tramite HTTP:
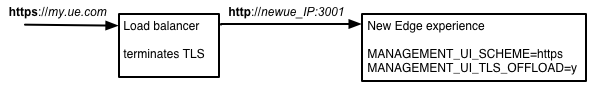
Questa configurazione è supportata ma devi configurare il bilanciatore del carico e la UI Edge di conseguenza.
Per configurare la UI Edge quando TLS termina sul bilanciatore del carico:
Modifica il file di configurazione che hai utilizzato per installare la UI Edge in imposta le seguenti proprietà TLS:
# Set to https to enable TLS MANAGEMENT_UI_SCHEME=https # Terminate TLS on a load balancer MANAGEMENT_UI_TLS_OFFLOAD=y # Set to the IP address or DNS name of the load balancer. MANAGEMENT_UI_IP=LB_IP_DNS # Set to the port number for the load balancer and Edge UI. # The load balancer and the Edge UI must use the same port number. MANAGEMENT_UI_IP=3001 # Leave these properties set to the same values as when you installed the Edge UI: MANAGEMENT_UI_PUBLIC_URIS=$MANAGEMENT_UI_SCHEME://$MANAGEMENT_UI_IP:$MANAGEMENT_UI_PORT SHOEHORN_SCHEME=http
Se imposti
MANAGEMENT_UI_TLS_OFFLOAD=y, omettiMANAGEMENT_UI_TLS_KEY_FILEeMANAGEMENT_UI_TLS_CERT_FILE.Vengono ignorate perché le richieste alla UI Edge arrivano tramite HTTP.Esegui questo comando per configurare TLS:
/opt/apigee/apigee-service/bin/apigee-service edge-management-ui configure-ssl -f configFile
Dove configFile è il nome del file di configurazione.
Lo script riavvia la UI Edge.
Esegui questi comandi per configurare e riavviare shoehorn:
/opt/apigee/apigee-service/bin/apigee-service edge-ui setup -f configFile
/opt/apigee/apigee-service/bin/apigee-service edge-ui restartDopo il riavvio, la UI Edge supporta l'accesso tramite HTTPS. Se non riesci ad accedere alla UI Edge dopo aver abilitato TLS, cancella il cache del browser e riprova ad accedere.
Disattiva TLS nell'interfaccia utente perimetrale
Per disattivare TLS nella UI Edge:
Modifica il file di configurazione che hai utilizzato per installare la UI Edge da impostare la seguente proprietà TLS:
# Set to http to disable TLS. MANAGEMENT_UI_SCHEME=http # Only if you had terminated TLS on a load balancer, # reset to the IP address or DNS name of the Edge UI. MANAGEMENT_UI_IP=newue_IP_DNS
Esegui questo comando per disabilitare TLS:
/opt/apigee/apigee-service/bin/apigee-service edge-management-ui configure-ssl -f configFile
Dove configFile è il nome del file di configurazione.
Lo script riavvia la UI Edge.
Esegui questi comandi per configurare e riavviare shoehorn:
/opt/apigee/apigee-service/bin/apigee-service edge-ui setup -f configFile
/opt/apigee/apigee-service/bin/apigee-service edge-ui restartOra puoi accedere alla UI Edge tramite HTTP. Se non riesci ad accedere alla UI Edge dopo aver disabilitato TLS, cancella il cache del browser e riprova ad accedere.
