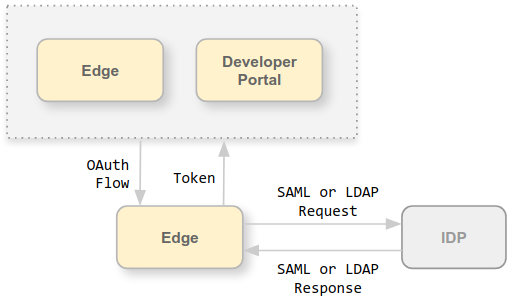
The Edge UI and Edge management API operate by making requests to the Edge Management Server, where the Management Server supports the following types of authentication:
- Basic authentication: Log in to the Edge UI or make requests to the Edge management API by passing your username and password.
- OAuth2: Exchange your Edge Basic Auth credentials for an OAuth2 access token and refresh token. Make calls to the Edge management API by passing the OAuth2 access token in the Bearer header of an API call.
Edge supports using the following external Identify Providers (IDPs) for authentication:
- Security Assertion Markup Language (SAML) 2.0: Generate OAuth access these from SAML assertions returned by a SAML identity provider.
- Lightweight Directory Access Protocol (LDAP): Use LDAP’s search and bind or simple binding authentication methods to generate OAuth access tokens.
Both SAML and LDAP IDPs support a single sign-on (SSO) environment. By using an external IDP with Edge, you can support SSO for the Edge UI and API in addition to any other services that you provide and that also support your external IDP.
The instructions in this section to enable external IDP support is different from the External authentication in the following ways:
- This section adds SSO support
- This section is for users of the Edge UI (not the Classic UI)
- This section is supported on 4.19.06 and later only
About Apigee SSO
To support SAML or LDAP on Edge, you install apigee-sso, the Apigee SSO module.
The following image shows Apigee SSO in an Edge for Private Cloud installation:
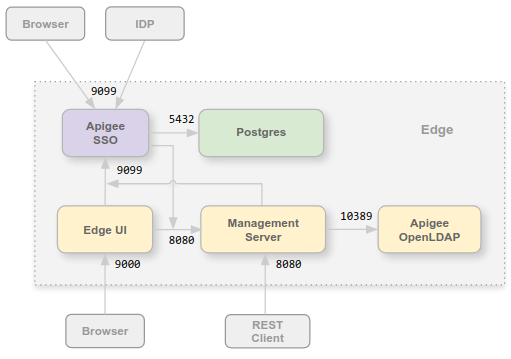
You can install the Apigee SSO module on the same node as the Edge UI and Management Server, or on its own node. Ensure that Apigee SSO has access to the Management Server over port 8080.
Port 9099 has to be open on the Apigee SSO node to support access to Apigee SSO from a browser, from the external SAML or LDAP IDP, and from the Management Server and Edge UI. As part of configuring Apigee SSO, you can specify that the external connection uses HTTP or the encrypted HTTPS protocol.
Apigee SSO uses a Postgres database accessible on port 5432 on the Postgres node. Typically you can use the same Postgres server that you installed with Edge, either a standalone Postgres server or two Postgres servers configured in master/standby mode. If the load on your Postgres server is high, you can also choose to create a separate Postgres node just for Apigee SSO.
Support added for OAuth2 to Edge for Private Cloud
As mentioned above, the Edge implementation of SAML relies on OAuth2 access tokens.Therefore, OAuth2 support has been added to Edge for Private Cloud. For more information, see Introduction to OAuth 2.0.
About SAML
SAML authentication offers several advantages. By using SAML you can:
- Take full control of user management. When users leave your organization and are deprovisioned centrally, they are automatically denied access to Edge..
- Control how users authenticate to access Edge. You can choose different authentication types for different Edge organizations.
- Control authentication policies. Your SAML provider may support authentication policies that are more in line with your enterprise standards.
- You can monitor logins, logouts, unsuccessful login attempts and high risk activities on your Edge deployment.
With SAML enabled, access to the Edge UI and Edge management API uses OAuth2 access tokens. These tokens are generated by the Apigee SSO module which accepts SAML assertions returned by the your IDP.
Once generated from a SAML assertion, the OAuth token is valid for 30 minutes and the refresh token is valid for 24 hours. Your development environment might support automation for common development tasks, such as test automation or Continuous Integration/Continuous Deployment (CI/CD), that require tokens with a longer duration. See Using SAML with automated tasks for information on creating special tokens for automated tasks.
About LDAP
The Lightweight Directory Access Protocol (LDAP) is an open, industry standard application protocol for accessing and maintaining distributed directory information services. Directory services may provide any organized set of records, often with a hierarchical structure, such as a corporate email directory.
LDAP authentication within Apigee SSO uses the Spring Security LDAP module. As a result, the authentication methods and configuration options for Apigee SSO’s LDAP support are directly correlated to those found in Spring Security LDAP.
LDAP with Edge for the Private Cloud supports the following authentication methods against an LDAP-compatible server:
- Search and Bind (indirect binding)
- Simple Bind (direct binding)
Apigee SSO attempts to retrieve the user's email address and update its internal user record with it so that there is a current email address on file as Edge uses this email for authorization purposes.
Edge UI and API URLs
The URL that you use to access the Edge UI and Edge management API is the same as used before you enabled SAML or LDAP. For the Edge UI:
http://edge_UI_IP_DNS:9000 https://edge_UI_IP_DNS:9000
Where edge_UI_IP_DNS is the IP address or DNS name of the machine hosting the Edge UI. As part of configuring the Edge UI, you can specify that the connection use HTTP or the encrypted HTTPS protocol.
For the Edge management API:
http://ms_IP_DNS:8080/v1 https://ms_IP_DNS:8080/v1
Where ms_IP_DNS is the IP address or DNS name of the Management Server. As part of configuring the API, you can specify that the connection use HTTP or the encrypted HTTPS protocol.
Configure TLS on Apigee SSO
By default, the connection to Apigee SSO uses HTTP over port 9099 on the node hosting
apigee-sso, the Apigee SSO module. Built into apigee-sso is a Tomcat
instance that handles the HTTP and HTTPS requests.
Apigee SSO and Tomcat support three connection modes:
- DEFAULT: The default configuration supports HTTP requests on port 9099.
- SSL_TERMINATION: Enabled TLS access to Apigee SSO on the port of your choice. You must specify a TLS key and cert for this mode.
- SSL_PROXY: Configures Apigee SSO in proxy mode, meaning you installed a
load balancer in front of
apigee-ssoand terminated TLS on the load balancer. You can specify the port used onapigee-ssofor requests from the load balancer.
Enable external IDP support for the portal
After enabling external IDP support for Edge, you can optionally enable it for Apigee Developer Services portal (or simply, the portal). The portal supports SAML and LDAP authentication when making requests to Edge. Note that this is different from SAML and LDAP authentication for developer login to the portal. You configure external IDP authentication for developer login separately. See Configure the portal to use IDPs for more.
As part of configuring the portal, you must specify the URL of the Apigee SSO module that you installed with Edge: