You're viewing Apigee Edge documentation.
Go to the
Apigee X documentation. info
Apigee Edge has several entry points that you might want to secure with TLS. In addition, Edge add-ons, such as the Developer Services portal, have entry points that can be configured to use TLS.
The Edge TLS configuration procedure depends on how you deployed Edge: Apigee Edge Cloud or Apigee Edge for Private Cloud.
Cloud-based deployment
In a Cloud-based deployment of Edge you are only responsible for configuring TLS access to API proxies and your target endpoints.
For the Cloud version of the Developer Services portal, you configure TLS on on the Pantheon hosting server.
For more, see Using TLS in a Cloud-based Edge installation.
Private Cloud deployment
For an Apigee Edge for Private Cloud installation of the Developer Services portal, you are completely responsible for configuring TLS. That means you not only have to obtain the TLS certificate and private key, but you also have to configure Edge to use TLS.
For more, see Using TLS in a Private Cloud installation.
Supported versions of TLS
The supported versions of TLS depend on whether you are using Edge in the Cloud or Edge for the Private Cloud:
- Edge in the Cloud: Supports TLS version 1.2 only. Support for TLS versions 1.0 and 1.1 for the Cloud have been retired. For more information, see TLS 1.0 and 1.1 retirement.
- Edge for the Private Cloud: Supports TLS versions 1.0, 1.1, and 1.2.
Where Edge uses TLS
The following images shows the places in an Edge installation where you can configure TLS:
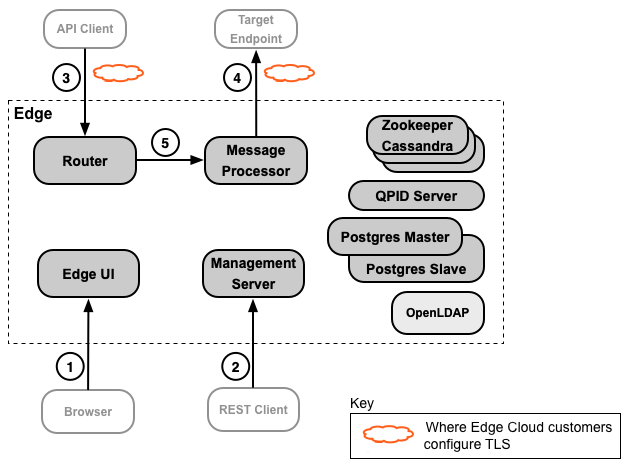
Apigee Edge for Private Cloud customers typically configure all connections to use TLS. However, for Cloud customers, Apigee handles most of the TLS configuration for you and only have to configure TLS for connections 3 and 4 shown in the figure.
The following table describes these TLS connections:
|
Source |
Destination |
Description |
|
|---|---|---|---|
|
1 |
API developer |
Edge management UI |
The Edge management UI is a browser-based tool that API developers use to perform most of the tasks necessary to create, configure, and manage API proxies and API products. |
|
2 |
API Developer |
Edge management API |
All Edge services can be configured through the Edge management API, a REST-based API. That means you can use these APIs to create, configure, and manage API proxies and API products, create and manage apps and app developers, and to perform many other types of operations. |
|
3 |
API Client (app) |
API |
Apps access your APIs by making requests to API proxies through virtual hosts on the Edge Router. |
|
4 |
Edge |
Target endpoint |
An API proxy functions as a mapping of a publicly available endpoint on Edge to a target endpoint, which is often defined by an endpoint on your backend service. The Edge Message Processor accesses your backend service in response to a request to an API proxy. |
|
5 |
Router |
Message Processor |
A Router handles all Edge incoming API traffic, determines the API proxy that handles the request, balances requests across available Message Processors, and dispatches the request. |
The Cloud-based version of Edge is typically configured so that all request from the API client are handled by the Router. Private Cloud customers can use a load balancer before the Router to handle requests. The following image shows a scenario where the API client accesses Edge through a load balancer, rather than accessing the Router directly:
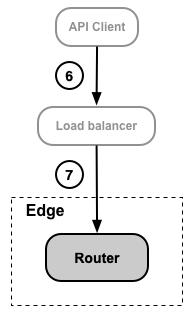
In a Private Cloud installation, the presence of a load balancer is dependent on your network configuration of Edge.
When using a load balancer, you can configure TLS between the API client and the load balancer and, if necessary, between the load balancer and the Router, as the following table describes:
|
Source |
Destination |
Description |
|
|---|---|---|---|
|
6 |
API Client (app) |
Load Balancer |
Apps access your APIs by making requests to API proxies through a load balancer. The load balancer forwards the request to an Edge Router. You can configure TLS on the entry point of the load balancer. The way you configure TLS is based on the load balancer. |
|
7 |
Load Balancer |
Router |
Depending on your configuration, you might configure TLS access to the Router from the load balancer. In that case, you configure TLS just as if the load balancer was not present. Or, if the load balancer and Router are in the same security domain, TLS configuration may not be necessary. However, that is dependent on your network configuration. |
Where the Developer Services portal uses TLS
The following image show the two places where the portal uses TLS:
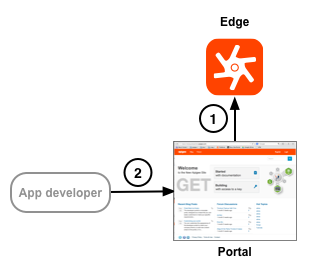
Apigee Edge for Private Cloud and Edge Cloud customers configure TLS on both connections. The following table describes these connections in more detail:
|
Source |
Destination |
Description |
|
|---|---|---|---|
|
1 |
Portal |
Edge management API |
The portal does not function as a stand-alone system. Instead, much of the information used by the portal is actually stored on Edge, where Edge can be deployed either in the Cloud or Edge for Private Cloud. The portal acts as the TLS client in this scenario by making requests to the Edge management API. As the TLS server, it is up to Edge to configure TLS. |
|
2 |
App developers |
Portal |
Developers log in to the portal to register apps and receive API keys. Because the connection requires the developer to pass login credentials, and for the portal to send app keys, it should be configured to use TLS. |
For more information on configuring TLS for the Cloud-based version and the Apigee Edge for Private Cloud version of the portal, see Using TLS on the portal.
