You're viewing Apigee Edge documentation.
Go to the
Apigee X documentation. info
What you'll learn
Through this tutorial, you'll learn to:
- Create an API proxy that requires an API key.
- Add an API product.
- Add a developer and register an app.
- Call your API with an API key.
It's important to protect your API from unauthorized access. One way to do that is with API keys (also called public keys, consumer keys or app keys).
When an app makes a request to your API, the app must supply a valid key. At runtime, the Verify API Key policy checks that the supplied API key:
- Is valid
- Hasn't been revoked
- Matches the API key for the API product that exposes the requested resources
If the key is valid, the request is allowed. If the key is invalid, the request results in an authorization failure.
In this tutorial, you'll create an API proxy that requires a valid API key to access it.
What you'll need
- An Apigee Edge account. If you don't have one yet, you can sign up with the directions at Creating an Apigee Edge account.
- A web browser to make an API call.
- (For the extra credit section, not required) cURL installed on your machine to make API calls from the command line.
Create the API proxy
- Go to https://apigee.com/edge and sign in.
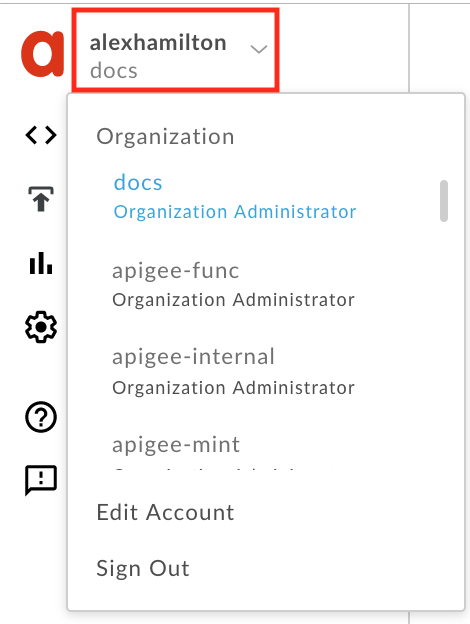
Switch to the organization you want by clicking your user name at the top of the side navigation bar to display the user profile menu, and then selecting the organization from the list.
-
Click API Proxies on the landing page to display the API proxies list.
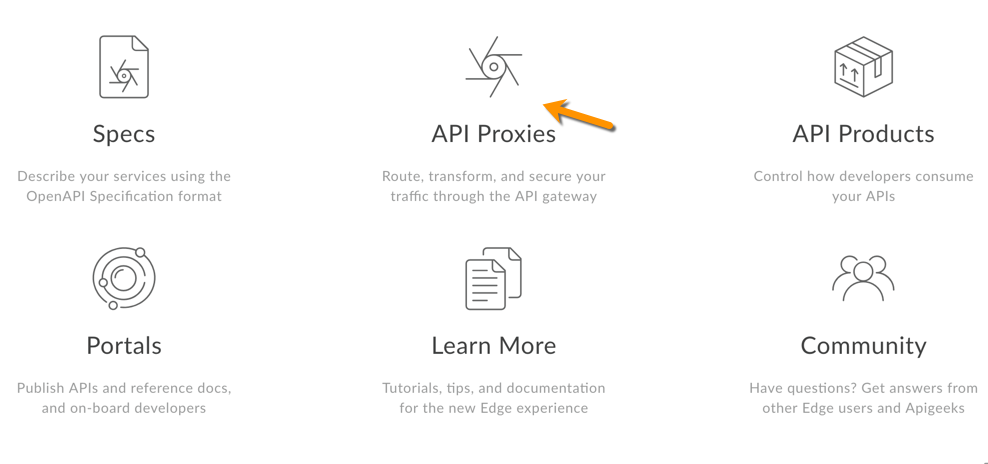
- Click + Proxy.

- On the Create Proxy page, select Reverse proxy (most common).
- On the Proxy Details page, configure the proxy as follows:
In this field do this Proxy Name Enter: helloworld_apikeyProject Base Path Change to:
/helloapikeyThe Project Base Path is part of the URL used to make requests to the API proxy.
Note: For Apigee's recommendations on API versioning, see Versioning in the Web API Design: The Missing Link e-book.
Existing API Enter:
http://mocktarget.apigee.netThis defines the target URL that Apigee Edge invokes on a request to the API proxy.
Description Enter: hello world protected by API key - Click Next.
- On the Common Policies page, for Security: Authorization, select API Key and then click Next. This will add two policies to your API proxy.
- On the Virtual Hosts page, select default and
secure and then click Next. Selecting default allows
you to call your API with
http://. Selecting secure, allows you to call your API withhttps://. - On the Summary page, make sure the test deployment environment is selected, and then click Create and deploy.
- You will see an acknowledgment that your new API proxy and an API product were created successfully, and that the API proxy was deployed to your test environment.
- Click Edit proxy to display the Overview page for the API proxy.
View the policies
- In the API proxy editor, click the Develop tab. You'll see that
two policies have been added to the request flow of the API proxy:
- Verify API Key: Checks the API call to make sure a valid API key is present (sent as a query parameter).
- Remove Query Param apikey: An AssignMessage policy that removes the API key after it's checked, so that it doesn't get passed around and exposed unnecessarily.
-
Click the Verify API Key policy icon in the flow view, and look at the policy's XML configuration in the lower code view. The
<APIKey>element tells the policy where it should look for the API key when the call is made. By default, it looks for the key as a query parameter calledapikeyin the HTTP request:<APIKey ref="request.queryparam.apikey" />
The name
apikeyis arbitrary and can be any property that contains the API key.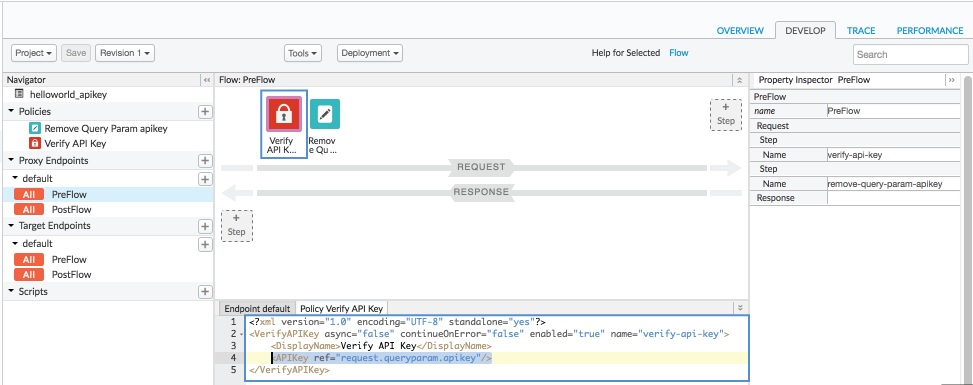
Try to call the API
In this step, you'll make a successful API call directly to the target service, then you'll make an unsuccessful call to the API proxy to see how it's being protected by the policies.
-
Success
In a web browser, go to the following address. This is the target service that the API proxy is configured to forward the request to, but you'll hit it directly for now:
http://mocktarget.apigee.net
You should get this successful response:
Hello, Guest! -
Failure
Now try to call your API proxy:
http://ORG_NAME-test.apigee.net/helloapikey
replacing
ORG_NAMEwith the name of your Edge organization.Without the Verify API Key policy, this call would give you the same response as the previous call. But in this case, you should get the following error response:
{"fault":{"faultstring":"Failed to resolve API Key variable request.queryparam.apikey","detail":{"errorcode":"steps.oauth.v2.FailedToResolveAPIKey"}}}
which means, correctly, that you didn't pass a valid API key (as a query parameter).
In the next steps, you'll add an API product.
Add an API product
To add an API product using the Apigee UI:
- Select Publish > API Products.
- Click +API Product.
Enter the Product details for your API product.
Field Description Name Internal name of the API product. Do not specify special characters in the name.
Note: You cannot edit the name once the API product is created. For example,helloworld_apikey-Product.Display name Display name for the API product. The display name is used in the UI and you can edit it at any time. If not specified, the Name value will be used. This field is auto-filled using the Name value; you can edit or delete its contents. The display name can include special characters. For example, helloworld_apikey-Product.Description Description of the API product. For example, Test product for tutorial.Environment Environments to which the API product will allow access. For example, testorprod.Access Select Public. Automatically approve access requests Enable automatic approval of key requests for this API product from any app. Quota Ignore for this tutorial. Allowed OAuth Scopes Ignore for this tutorial. - In the API resources section, select the API proxy you just
created. For example,
helloworld_apikey. - Click Add.
- In the Paths section, add the path "/".
- Click Add.
- Click Save.
In the next steps, you'll get the required API key.
Add a developer and app to your organization
Next, we're going to simulate the workflow of a developer signing up to use your APIs. A developer will have one or more apps that call your APIs, and each app gets a unique API key. This gives you, the API provider, more granular control over access to your APIs and more granular reporting on API traffic by app.
Create a developer
To create a developer:
- Select Publish > Developers in the menu.
- Click + Developer.
Enter the following in the New Developer window:
In this field enter First Name KeyserLast Name SozeUsername keyserEmail keyser@example.com- Click Create.
Register an app
To register a developer app:
- Select Publish > Apps.
- Click + App.
Enter the following in the New App window:
In this field do this Name and Display Name Enter: keyser_appCompany / Developer Select: DeveloperDeveloper Select: Keyser Soze (keyser@example.com)Callback URL and Notes Leave blank - In the Credentials section, select Never from the Expiry menu. The credentials for this app will never expire.
- Under Products, click Add product.
- Select helloworld_apikey-Product.
- Click Add.
- Click Create above and to the right of the App Details section to save your work.
Get the API key
To get the API key:
- On the Apps page (Publish > Apps), click keyser_app.
On the keyser_app page, click Show next to Key in the Credentials section. In the Product section, notice that the key is associated with helloworld_apikey
.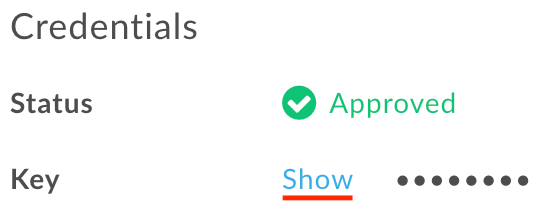
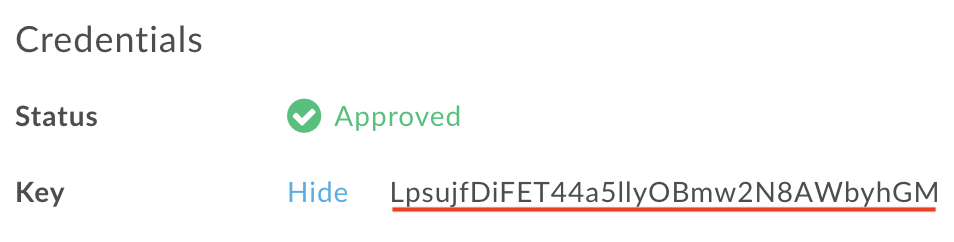
- Select and copy the Key. You'll use it in the next step.
Call the API with a key
Now that you have an API key, you can use it to call the API proxy. Enter the following in your web browser. Substitute your Edge organization name for ORG_NAME, and the API key for API_KEY below. Make sure there are no extra spaces in the query parameter.
http://ORG_NAME-test.apigee.net/helloapikey?apikey=API_KEY
Now when you call to the API proxy, you should get this response:
Hello, Guest!
Congratulations! You've created an API proxy and protected it by requiring that a valid API key be included in the call.
Note that in general it's not good practice to pass an API key as a query parameter. You should consider passing it in the HTTP header instead.
Best practice: Passing the key in the HTTP header
In this step, you will modify the proxy to look for the API key in a
header called x-apikey.
- Edit the API proxy. Select Develop > API Proxies > helloworld_apikey, and go to the Develop view.
-
Select the Verify API Key policy, and modify the policy XML to tell the policy to look in the
headerrather than in thequeryparam:<APIKey ref="request.header.x-apikey"/>
- Save the API proxy to deploy the change.
-
Make the following API call using cURL to pass the API key as a header called
x-apikey. Don't forget to substitute your organization name.curl -v -H "x-apikey: API_KEY" http://ORG_NAME-test.apigee.net/helloapikey
Note that to fully complete the change, you'd also need to configure the AssignMessage policy to remove the header instead of the query parameter. For example:
<Remove>
<Headers>
<Header name="x-apikey"/>
</Headers>
</Remove>
Related topics
Here are some topics that directly relate to this tutorial:
- Manage API products
- API keys
- Register app developers
- Register apps and manage API keys
- VerifyAPIKey policy
- AssignMessage policy
Going a bit deeper, protecting APIs with API keys is only part of the story. Oftentimes, API protection involves additional security such as OAuth.
OAuth is an open protocol that, in a nutshell, exchanges credentials (like username and password) for access tokens. Access tokens are long, random strings that can be passed around a message pipeline, even from app to app, without compromising the original credentials. Access tokens often have short lives, so new ones are always being generated.
Except as otherwise noted, the content of this page is licensed under the Creative Commons Attribution 4.0 License, and code samples are licensed under the Apache 2.0 License. For details, see the Google Developers Site Policies. Java is a registered trademark of Oracle and/or its affiliates.
Last updated 2026-02-02 UTC.
