You're viewing Apigee Edge documentation.
Go to the
Apigee X documentation. info
SourceNotConfigured
Error Message
Deployment of the API proxy through either the Edge UI or Edge management API fails with this error message:
Error Deploying Revision revision_number to environment ValidateSAMLAssertion[policy_name]: Source is not correctly configured.
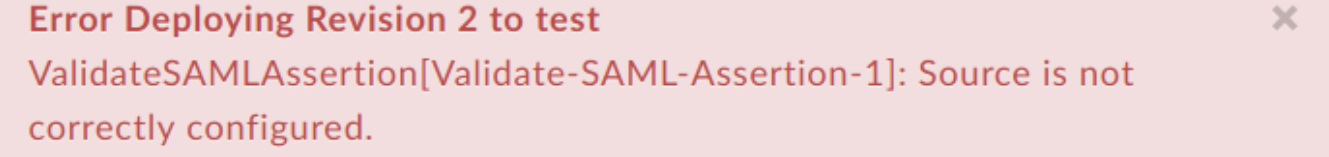
Example Error Message
Error Deploying Revision 2 to test
ValidateSAMLAssertion[Validate-SAML-Assertion-1]: Source is not correctly configured.
Example Error Screenshot
Cause
The deployment of the API Proxy fails with this error if one or more of
the following elements of the Validate SAML Assertion policy is not
defined or empty: <Source>, <XPath>, <Namespaces>, <Namespace>.
For example, if you miss the <XPath> element or leave the <Source>
element or its entities empty, then the deployment of the API proxy fails.
Diagnosis
Identify the failed Validate SAML Assertion policy name from the error message. For example, in the following error the Validate SAML Assertion policy name is
Validate-SAML-Assertion-1.ValidateSAMLAssertion[Validate-SAML-Assertion-1]: Source is not correctly configured.Examine the failed Validate SAML Assertion policy XML. Check if one or more of the following elements of the policy is missing or empty:
<Source>,<XPath>,<Namespaces>,<Namespace>. If so, that could be the cause of the error.For example, the following policy has an empty
<Namespaces>element under the<Source>element:<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <ValidateSAMLAssertion name="SAML" ignoreContentType="false"> <Source name="request"> <Namespaces></Namespaces> </Source> <Description/> <TrustStore>ref://TrustStoreName</Truststore> <RemoveAssertion>false</RemoveAssertion> </ValidateSAMLAssertion>In the above example, the
<Namespaces>element is empty, therefore you get the error:ValidateSAMLAssertion[Validate-SAML-Assertion-1]: Source is not correctly configured.
Resolution
Ensure that values of the <Source> element are configured correctly
with the <Namespaces> element and its child element <Namespace>.
You also need to ensure the <XPath> element is defined and non-empty.
To correct the example Validate SAML Assertion policy shown above, you
could add the <Namespace> elements as well as <XPath>:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<ValidateSAMLAssertion name="SAML" ignoreContentType="false">
<Source name="request">
<Namespaces>
<Namespace prefix='soap'>http://schemas.xmlsoap.org/soap/envelope/</Namespace>
<Namespace prefix='wsse'>http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd</Namespace>
<Namespace prefix='saml'>urn:oasis:names:tc:SAML:2.0:assertion</Namespace>
</Namespaces>
<XPath>/soap:Envelope/soap:Header/wsse:Security/saml:Assertion</XPath>
</Source>
<Description/>
<TrustStore>ref://TrustStoreName</Truststore>
<RemoveAssertion>false</RemoveAssertion>
</ValidateSAMLAssertion>
TrustStoreNotConfigured
Error Message
Deployment of the API proxy through either the Edge UI or Edge management API fails with this error message:
Error Deploying Revision revision_number to environment ValidateSAMLAssertion[[Ljava.lang.Object;@object]: Trust store is not correctly configured.
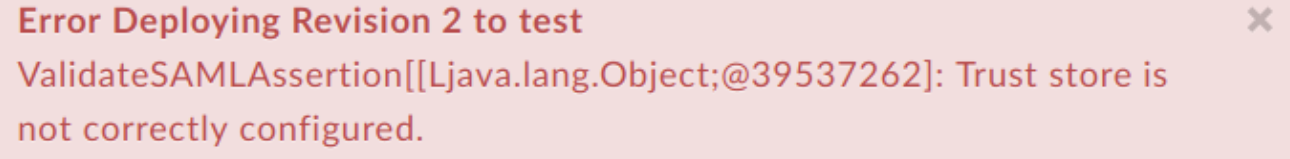
Example Error Message
Error Deploying Revision 2 to test
ValidateSAMLAssertion[[Ljava.lang.Object;@39537262]: Trust store is not correctly configured.
Example Error Screenshot
Cause
If the <TrustStore> element is empty or not specified in the
ValidateSAMLAssertion policy, then the deployment of the API
proxy fails. A valid Trust Store is required.
Diagnosis
Examine all the Validate SAML Assertion policies in the specific API Proxy where the failure has occurred. If there is any Validate SAML Assertion policy in which the
<TrustStore>element is empty or not specified, then that's the cause of the error.<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <ValidateSAMLAssertion name="SAML" ignoreContentType="false"> <Source name="request"> <Namespaces> <Namespace prefix='soap'>http://schemas.xmlsoap.org/soap/envelope/</Namespace> <Namespace prefix='wsse'>http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd</Namespace> <Namespace prefix='saml'>urn:oasis:names:tc:SAML:2.0:assertion</Namespace> </Namespaces> <XPath>/soap:Envelope/soap:Header/wsse:Security/saml:Assertion</XPath> </Source> <Description/> <TrustStore/> <RemoveAssertion>false</RemoveAssertion> </ValidateSAMLAssertion>
Resolution
Ensure that the element <TrustStore> is always specified and
non-empty within the Validate SAML Assertion policy. The <TrustStore>
name should match the name of a valid TrustStore
that exists in all the environments to which you are attempting to deploy
a proxy.
To correct the above example, you can specify the <TrustStore>
element with a valid value.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<ValidateSAMLAssertion name="SAML" ignoreContentType="false">
<Source name="request">
<Namespaces>
<Namespace prefix='soap'>http://schemas.xmlsoap.org/soap/envelope/</Namespace>
<Namespace prefix='wsse'>http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd</Namespace>
<Namespace prefix='saml'>urn:oasis:names:tc:SAML:2.0:assertion</Namespace>
</Namespaces>
<XPath>/soap:Envelope/soap:Header/wsse:Security/saml:Assertion</XPath>
</Source>
<TrustStore>TrustStoreName</TrustStore>
<RemoveAssertion>false</RemoveAssertion>
</ValidateSAMLAssertion>
Refer to Truststores and Keystores for more information on how to use Truststore.
NullKeyStore
Error Message
Deployment of the API proxy through either the Edge UI or Edge management API fails with this error message:
Error Deploying Revision revision_number to environment Assertion KeyStore name cannot be null.
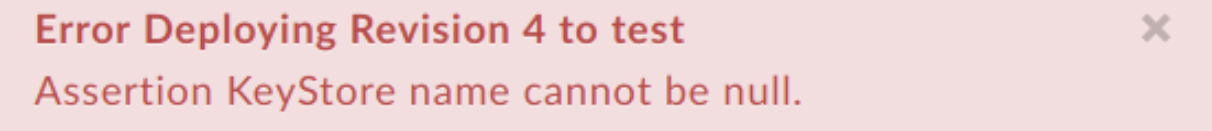
Example Error Message
Error Deploying Revision 4 to test
Assertion KeyStore name cannot be null.
Example Error Screenshot
Cause
If the child element <Name> is empty or not specified in the
<Keystore> element of GenerateSAMLAssertion policy, then the
deployment of the API proxy fails. A valid Keystore name is required.
Diagnosis
Examine all the Generate SAML Assertion policies in the specific API Proxy where the failure has occurred. If there is any Generate SAML Assertion policy in which the child element
<Name>is empty or not specified in the<Keystore>element, then that's the cause of the error.The following Generate SAML Assertion policy has an empty child element
<Name>in the<Keystore>element:<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <GenerateSAMLAssertion name="SAML" ignoreContentType="false">` <CanonicalizationAlgorithm /> <Issuer ref="reference">Issuer name</Issuer> <KeyStore> <Name></Name> <Alias ref="reference">alias</Alias> </KeyStore> <OutputVariable> <FlowVariable>assertion.content</FlowVariable> <Message name="request"> <Namespaces> <Namespace prefix="test">http://www.example.com/test</Namespace> </Namespaces> <XPath>/envelope/header</XPath> </Message> </OutputVariable> <SignatureAlgorithm /> <Subject ref="reference">Subject name</Subject> <Template ignoreUnresolvedVariables="false"> <!-- A lot of XML goes here, in CDATA, with {} around each variable --> </Template> </GenerateSAMLAssertion>
Resolution
Ensure that the child element <Name> is always specified and
non-empty within the <Keystore> element of the Generate SAML Assertion
policy.
To correct the above example, you can specify the <Name> element correctly
as well as ensure that a valid value is specified to the <Alias> element.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<GenerateSAMLAssertion name="SAML" ignoreContentType="false">
<CanonicalizationAlgorithm />
<Issuer ref="reference">Issuer name</Issuer>
<KeyStore>
<Name ref="reference">keystorename</Name>
<Alias ref="reference">alias</Alias>
</KeyStore>
<OutputVariable>
<FlowVariable>assertion.content</FlowVariable>
<Message name="request">
<Namespaces>
<Namespace prefix="test">http://www.example.com/test</Namespace>
</Namespaces>
<XPath>/envelope/header</XPath>
</Message>
</OutputVariable>
<SignatureAlgorithm />
<Subject ref="reference">Subject name</Subject>
<Template ignoreUnresolvedVariables="false">
<!-- A lot of XML goes here, in CDATA, with {} around
each variable -->
</Template>
</GenerateSAMLAssertion>
Refer to examples from Code Samples in SAMLAssertion Policy Reference Article.
NullKeyStoreAlias
Error Message
Deployment of the API proxy through either the Edge UI or Edge management API fails with this error message:
Error Deploying Revision revision_number to environment Assertion KeyStore alias cannot be null.
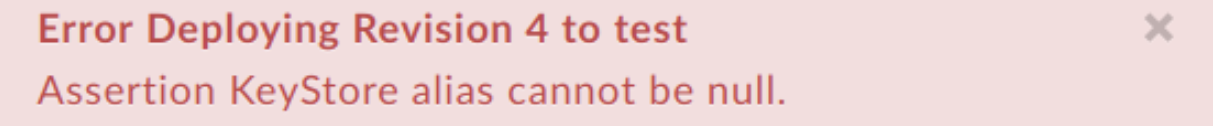
Example Error Message
Error Deploying Revision 4 to test
Assertion KeyStore alias cannot be null.
Example Error Screenshot
Cause
If the child element <Alias> is empty or not specified in the
<Keystore> element of Generate SAML Assertion policy, then the
deployment of the API proxy fails. A valid Keystore alias is required.
Diagnosis
Examine all the Generate SAML Assertion policies in the specific API Proxy where the failure has occurred. If there is any Generate SAML Assertion policy in which the child element
<Alias>is empty or not specified in the<Keystore>element, then that's the cause of the error.The following Generate SAML Assertion policy has an empty child element
<Alias>in the<Keystore>element:<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <GenerateSAMLAssertion name="SAML" ignoreContentType="false">` <CanonicalizationAlgorithm /> <Issuer ref="reference">Issuer name</Issuer> <KeyStore> <Name ref="reference">keystorename</Name> <Alias></Alias> </KeyStore> <OutputVariable> <FlowVariable>assertion.content</FlowVariable> <Message name="request"> <Namespaces> <Namespace prefix="test">http://www.example.com/test</Namespace> </Namespaces> <XPath>/envelope/header</XPath> </Message> </OutputVariable> <SignatureAlgorithm /> <Subject ref="reference">Subject name</Subject> <Template ignoreUnresolvedVariables="false"> <!-- A lot of XML goes here, in CDATA, with {} around each variable --> </Template> </GenerateSAMLAssertion>
Resolution
Ensure that the child element <Name> is always specified and non-empty
within the <Keystore> element of the Generate SAML Assertion policy.
To correct the above example, you can specify the <Alias> element
correctly as well as ensure that a valid value is specified to the
<Name> element.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<GenerateSAMLAssertion name="SAML" ignoreContentType="false">
<CanonicalizationAlgorithm />
<Issuer ref="reference">Issuer name</Issuer>
<KeyStore>
<Name ref="reference">keystorename</Name>
<Alias ref="reference">alias</Alias>
</KeyStore>
<OutputVariable>
<FlowVariable>assertion.content</FlowVariable>
<Message name="request">
<Namespaces>
<Namespace prefix="test">http://www.example.com/test</Namespace>
</Namespaces>
<XPath>/envelope/header</XPath>
</Message>
</OutputVariable>
<SignatureAlgorithm />
<Subject ref="reference">Subject name</Subject>
<Template ignoreUnresolvedVariables="false">
<!-- A lot of XML goes here, in CDATA, with {} around
each variable -->
</Template>
</GenerateSAMLAssertion>
Refer to examples from Code Samples in SAMLAssertion Policy Reference Article.
NullIssuer
Error Message
Deployment of the API proxy through either the Edge UI or Edge management API fails with this error message:
Error Deploying Revision revision_number to environment Assertion Issuer cannot be null.
Example Error Message
Error Deploying Revision 4 to test
Assertion Issuer cannot be null.
Example Error Screenshot
Cause
If the <Issuer> element is empty or not specified in the Generate SAML
Assertion policy, then the deployment of the API proxy fails. A valid
<Issuer> value is required.
Diagnosis
Examine all the Generate SAML Assertion policies in the specific API Proxy where the failure has occurred. If there is any Generate SAML Assertion policy in which the
<Issuer>element is empty or not specified, then that's the cause of the error.The following Generate SAML Assertion policy has an empty
<Issuer>element:<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <GenerateSAMLAssertion name="SAML" ignoreContentType="false">` <CanonicalizationAlgorithm /> <Issuer></Issuer> <KeyStore> <Name ref="reference">keystorename</Name> <Alias ref="reference">alias</Alias> </KeyStore> <OutputVariable> <FlowVariable>assertion.content</FlowVariable> <Message name="request"> <Namespaces> <Namespace prefix="test">http://www.example.com/test</Namespace> </Namespaces> <XPath>/envelope/header</XPath> </Message> </OutputVariable> <SignatureAlgorithm /> <Subject ref="reference">Subject name</Subject> <Template ignoreUnresolvedVariables="false"> <!-- A lot of XML goes here, in CDATA, with {} around each variable --> </Template> </GenerateSAMLAssertion>
Resolution
Ensure that the <Issuer> element is always specified and non-empty in
the Generate SAML Assertion policy.
To correct the above example, specify the <Issuer> element correctly:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<GenerateSAMLAssertion name="SAML" ignoreContentType="false">
<CanonicalizationAlgorithm />
<Issuer ref="reference">Issuer name</Issuer>
<KeyStore>
<Name ref="reference">keystorename</Name>
<Alias ref="reference">alias</Alias>
</KeyStore>
<OutputVariable>
<FlowVariable>assertion.content</FlowVariable>
<Message name="request">
<Namespaces>
<Namespace prefix="test">http://www.example.com/test</Namespace>
</Namespaces>
<XPath>/envelope/header</XPath>
</Message>
</OutputVariable>
<SignatureAlgorithm />
<Subject ref="reference">Subject name</Subject>
<Template ignoreUnresolvedVariables="false">
<!-- A lot of XML goes here, in CDATA, with {} around
each variable -->
</Template>
</GenerateSAMLAssertion>
Refer to examples from Code Samples in SAMLAssertion Policy Reference Article.
