You're viewing Apigee Edge documentation.
Go to the
Apigee X documentation. info
Since the previous Edge for Private Cloud Feature Release, the following releases have occurred and are included in this Feature Release:
| Edge UI release | Edge management release |
|---|---|
See About release numbering to understand how you can figure out whether a specific cloud release is included in your version of Edge for Private Cloud.
Release overview
The most important new feature in this release is the addition of support for Security Assertion Markup Language (SAML) 2.0 as the authentication mechanism for Edge, API BaaS, and the Developer Services portal. By using SAML with Edge, you can support SSO for the Edge UI and API in addition to any other services that you provide and that also support SAML.
SAML authentication offers several advantages. By using SAML you can:
- Take full control of user management. When users leave your organization and are deprovisioned centrally, they are automatically denied access to Edge..
- Control how users authenticate to access Edge. You can choose different authentication types for different Edge organizations.
- Control authentication policies. Your SAML provider may support authentication policies that are more in line with your enterprise standards.
- You can monitor logins, logouts, unsuccessful login attempts and high risk activities on your Edge deployment.
- Note that SAML is only used for authentication. Authorization is still controlled by Edge user roles.
See Supporting SAML on Edge for Private Cloud for more.
This release includes a number of other notable features, including:
- Ability to migrate the Developer Services portal from Apache/MySQL to Postgres/Nginx
- Command to disable TLS in the Edge UI
- New properties to configure the Edge installation
- Custom consumer key and secret naming rules
- Support for Red Hat/CentOS version 7.4
The remainder of this topic contains details on all the new features, updates, and bug fixes contained in the release.
Deprecations and retirements
The following features were deprecated or retired in this release. See the Edge deprecation policy for more information.
Deprecations
Deprecation of Apigee secure store (vaults)
The Apigee secure store, also known as "vaults," is being deprecated and will be retired in April of 2018. Vaults, which provide encrypted storage of key/value pairs, are created with the management API and accessed at runtime with functions in the apigee-access Node.js module.
Instead of using the secure store, use encrypted key value maps (KVMs), as described in Working with key value maps. Encrypted KVMs are just as secure as vaults and provide more options for creation and retrieval. (MGMT-3848)
Deprecation for adding paths on the API proxy Performance tab
Up to this release, you could navigate to an API proxy in the management UI, go to the Performance tab, and create different paths for a chart-based comparison on the proxy's Performance tab and in the Business Transactions dashboard. This feature is now retired and is no longer available in the UI. For an alternative to this functionality, see the following Apigee Community article: Alternative to Business Transactions API. (EDGEUI-902)
New features and updates
Following are the new features and enhancements in this release. In addition to the following enhancements, this release also contains multiple usability, performance, security, and stability enhancements.
Private Cloud
SAML support added to Edge, API BaaS, and Developer Services portal
Edge now supports Security Assertion Markup Language (SAML) 2.0 as the authentication mechanism for Edge, API BaaS, and the Developer Services portal. SAML supports a single sign-on (SSO) environment. By using SAML, you can support SSO for Edge in addition to any other services that you provide and that also support SAML.
See Supporting SAML on Edge for Private Cloud.
Added apigee-ssoadminapi.sh utility
After enabling SAML, you now use the new apigee-ssoadminapi.sh to perform many administrative tasks, such as creating users and organizations.
See Using apigee-ssoadminapi.sh.
(DOS-5118)
Can now migrate Developer Services portal from Apache/MySQL/MariaDB to Nginx/postgres
A .tar based installation of the Developer Services portal uses Apache and MySQL or MariaDB. You can now migrate your existing installation of the portal to use Nginx and Postgres. This migration is required if you want to update to portal version 4.17.09.
See Convert a tar-based portal to an RPM-based portal.
Added support for Red Hat/CentOS version 7.4
You can now deploy Edge for the Private Cloud, API BaaS, and the Developer Services portal on Red Hat/CentOS version 7.4.
See Supported software and supported versions.
Added property to cause the installer check CPU and memory requirements during install
The Edge installation configuration file now supports the following property:
ENABLE_SYSTEM_CHECK=y If "y", the installer check that the system meets the CPU and memory requirements for the component being installed. See Installation Requirements for requirements for each component. The default value is "n" to disable check.
See Edge Configuration File Reference.
(DOS-4772)
Added property to let you select the IP address used by the installer on a server has multiple interface cards
If a server has multiple interface cards, the "hostname -i" command returns a space-separated list of IP addresses's. By default, the Edge installer uses the first IP address returned, which might not be correct in all situations. As an alternative, you can set the following property in the installation configuration file:
ENABLE_DYNAMIC_HOSTIP=y
With that property set to "y", the installer prompts you to select the IP address to use as part of the install. The default value is "n".
See Edge Configuration File Reference.
(DOS-5117)
New UI options and APIs available for configuring TLS
The Beta release of the new self-service TLS/SSL feature for the Cloud is now available in the Private Cloud as a Beta feature. Using this Beta you can:
- Create, modify, and delete keystores and truststores in the UI as well as the API
- Upload TLS certs as PKCS12/PFX
- Generate self-signed certs from the UI or API
- Test the validity of a keystore or truststore in the UI
The Beta documentation (PDF) for these features is available at:
- Using the Edge Cloud UI to create Keystores and Truststores
- Using the Edge API to create Keystores and Truststores
For complete details, refer to the additional documentation (PDF):
- Options for configuring TLS
- Configuring TLS access to an API for the Cloud
- Configuring TLS from Edge to the backend
- Update a TLS certificate for the Cloud
(EDGEUI-1058)
Added obfuscated password command
Added a command to generate an obfuscated password so any component can generate an encrypted password. You can generate an obfuscated password by using the following command on the Edge Management Server:
> /opt/apigee/apigee-service/bin/apigee-service edge-management-server generate-obfuscated-password
Enter the new password, and then confirm it at the prompt. For security reasons, the text of the password is not displayed. This command returns the password in the form:
OBF:58fh40h61svy156789gk1saj MD5:902fobg9d80e6043b394cb2314e9c6
See Configuring TLS/SSL for Edge On Premises.
(TBD-250)
Added new command to obfuscate the new password when changing an organization user's password
To reset the password for an organization user, you now use the apigee-service utility to invoke apigee-openldap:
> /opt/apigee/apigee-service/bin/apigee-service apigee-openldap change-ldap-user-password -u userEmail
You are prompted for the system admin's password, and then for the new user password. For security reasons, the text of the passwords is not displayed as you enter them.
(DBS-1733)
Add command to disable TLS in the Edge UI
You can now use the following command to disable TLS in the Edge UI:
/opt/apigee/apigee-service/bin/apigee-service edge-ui disable-ssl
See Configuring TLS for the management UI.
(EDGEUI-1114)
Added property to control the format of timestamp in log messages
By default, the timestamp in log messages created by the Message Logging policy has the format:
yyyy-MM-dd'T'HH:mm:ss.sssZ
For example:
2017-05-08T13:33:00.000+0000
You can use the conf_system_apigee.syslogger.dateFormat property on the Edge Message Processor to control that format.
(APIRT-4196)
Added new required SMTP configuration parameter to API BaaS installation
You must now use the SMTPMAILFROM parameter in the API BaaS installation configuration file. This parameter specifies the email address used when API BaaS sends automated emails, such as when a user requests to reset a password.
See BaaS Configuration File Reference.
(APIBAAS-2103)
Added support to allow the Edge Router and Nginx web server for the portal to access ports below 1000
You can now use the Router and Nginx web server for the portal to access ports below 1000 without having to run them as a different user. in previous releases, the Router and Nginx web server could not access ports below 1000 without running them as a special user.
Changed how to configure the logging level for the Edge UI
The properties used to configure the logging level for the Edge UI have changed. See Setting the log level for an Edge component for the new properties and procedure.
(EDGEUI-886)
API Services
Custom consumer key and secret naming rules
Naming rules and validation have been updated for creating a custom consumer key and secret for a developer app. Consumer keys and secrets can contain letters, numbers, underscores, and hyphens. No other special characters are allowed.
The custom key/secret creation process is more fully documented in Import existing consumer keys and secrets. (MGMT-3916)
Keystore and Target Server name validation
The names of keystores and Target Servers can be 255 characters max and can contain letters, numbers, spaces, hyphens, underscores, and periods. Edge now validates this at create time. (MGMT-4098)
Bugs fixed
The following bugs are fixed in this release. This list is primarily for users checking to see if their support tickets have been fixed. It's not designed to provide detailed information for all users.
Private Cloud 4.17.09
| Issue ID | Description |
|---|---|
| APIRT-4346 |
Edge Router now working on FIPS-enabled server The Edge Router can now be deployed to a server that supports FIPS (Federal Information Processing Standards). |
| APIRT-4726 |
ScriptableHttpClient should not assume a message context is still present at send time Now ScriptableHttpClient reads the message context at start time. |
|
DBS-1529 |
Cassandra backup script no longer stops/restarts Cassandra Previously, the Cassandra backup script stopped and then restarted the Cassandra server as part of the backup process. The script no longer performs this stop/restart and leaves the Cassandra server running during the backup process. |
| DOS-5100 |
installer now sets Postgres password based on value specified in PG_PWD in previous releases, the Postgres password was not set properly based on the value of PG_PWD in the config file. |
| EDGESERV-7 |
Updated Node.js default properties Node.js now uses the following default values for properties on the Private Cloud installation: connect.ranges.denied= connect.ranges.allowed= connect.ports.allowed= This means Edge for Private Cloud no longer restricts Node.js code from accessing certain IP addresses by default. See Understanding Edge support for Node.js modules for more. |
| EDGEUI-1110 |
Cannot see the resource names when creating proxy using OpenAPI Resource names are now appearing correctly when creating proxy using OpenAPI. |
| MGMT-4021 |
Management Server up API call now returns properly formatted response The /v1/servers/self/up API call now returns properly formatted xml or json instead of always returning text. |
| MGMT-4294 |
Proxy and product names containing spaces or hyphens causing permissions issue Proxy and product names now work correctly when the name contains a space or hyphen. |
Cloud 17.08.16 (UI)
| Issue ID | Description |
|---|---|
| 64530444 | Treat YAML files as editable in API proxy editor YAML files can now be edited using the API proxy editor. When you open a YAML file in the editor, an error message is no longer displayed. |
| 64479253 | Fix logs button enabled on Trace tab The Node.js Logs button will only display on the Trace page when the API proxy has Node source files. |
| 64441949 | Fix download issue on GeoMap analytics dashboard Fixed issue that was preventing the CSV file to be downloaded on the GeoMap analytics dashboard. |
| 64122687 | OpenAPI Specifications without operationIDs generates flows with names
"undefined" When generating an API proxy from an OpenAPI Specification that has no operationIDs defined, the path and verb are now used for the conditional flow name. |
Cloud 17.08.14 (API management and runtime)
| Issue ID | Description |
|---|---|
| APIRT-4584 | Flow hook not deploying consistently, ZooKeeper check not working |
| APIRT-3081 | messaging.adaptors.http.flow.ServiceUnavailable error with Concurrent Rate Limit policy |
Cloud 17.07.31 (API management)
| Issue ID | Description |
|---|---|
| MGMT-4141 |
Encrypted values in KVM not decrypted even when retrieved with private
prefix.
|
Cloud 17.07.17 (API management and runtime)
| Issue ID | Description |
|---|---|
| APIRT-4400 | "Apigee Router" is displayed in nginx response |
| APIRT-4155 | ExtractVariables policy does not handle malformed form parameters in POST body |
| APIRT-3954 |
HTTP Health check should not execute more than once a second.
This fix resolves an issue in which a large number of health checks impeded performance. |
| APIRT-3928 | "nginx" is included in message returned from request |
| APIRT-3729 | Apigee modifies proxy.client.ip variable after AssignMessage policy removes x-forwarded-for header |
| APIRT-3546 | When using AssignMessage policy to create a new message, Trace does not indicate a new message has been assigned |
| APIRT-1873 | Southbound SSL shouldn't fall back on JDK trust store in the absence of configured trust store |
| APIRT-1871 | Southbound : Certificate common name is not validated vs the hostname in the URL |
Cloud 17.06.20 (UI)
| Issue ID | Description |
|---|---|
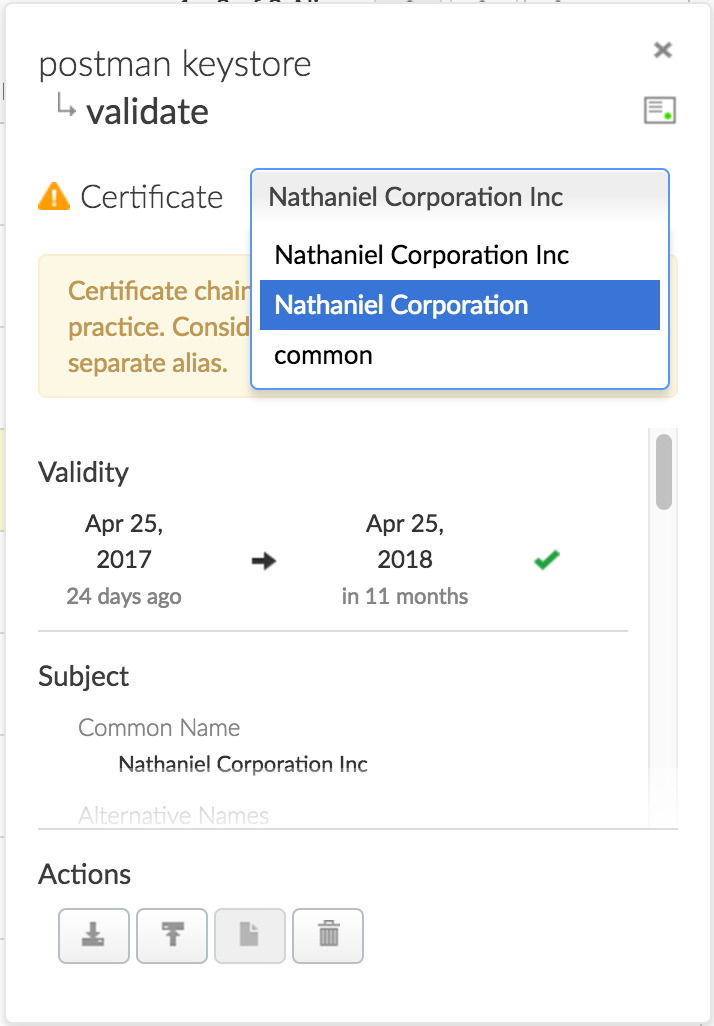
| EDGEUI-1087 | Remove chain cert warning messages from self-service TLS UI The certificate chain warning indications have been removed from the UI. Alias rows which contain certificate chains will now display the data for the certificate closest to expiry in the "Expiration" and "Common Name" columns. The warning banner under the certificate selector of the alias panel has been changed into an informative annotation. |
Cloud 17.06.14 (UI)
| Issue ID | Description |
|---|---|
| EDGEUI-1092 | Actions in keystores alias panel do not work In the Beta version of the new TLS keystores UI, when viewing the alias panel, the Actions buttons did not always work. This issue has been fixed. |
| EDGEUI-1091 | After updating an alias certificate, alias panel is broken In the Beta version of the new TLS keystores UI, after updating an alias certificate, the alias panel would sometimes encounter an error and need to be refreshed in order to display the alias details. This issue has been fixed. |
| EDGEUI-1088 | Clicking Edit button on User Settings page results in 404 When editing your user account settings, you are now directed to the two-factor authentication configuration page. For more information, see Enable two-factor authentication for your Apigee account. In order to update your password, you must sign out of your account and click Reset Password on the login page. |
| EDGEUI-1082 | Keystores list does not handle * selector Wildcard selectors were not working in the keystores list filtering input. This issue has been fixed. |
| EDGEUI-1079 | Hide keys field in developer details for CPS organizations For CPS organizations, the keys field is not displayed on the developer details page. |
| EDGEUI-1074 | When viewing chained certs, cert validity icon only represents head
cert The cert validity icon now represents the currently selected cert, instead of always representing the head cert. |
| UAP-328 | Latency analysis filter dropdown to show all API proxies API proxies will no longer be removed from the Proxy filter dropdown which has happened in the past in certain situations. If you select an API proxy that has no data for the selected time interval, No data to show is now displayed. |
Cloud 17.05.22.01 (Monetization)
| Issue ID | Description |
| DEVRT-3647 |
Transaction status API usability improvements
The following usability improvements have been made to the transaction status API, described in View the status of transactions.
In addition, an issue with the transaction status API has been fixed. |
Cloud 17.05.22 (UI)
| Issue ID | Description |
|---|---|
| EDGEUI-1027 |
Keystore/Truststore alias panel should display details for each certificate in a
certificate chain If you upload a certificate chain to an alias, when viewing the alias panel, you can now select each certificate from a dropdown to view its details.
Note: Certificate chaining is not a recommended best practice. Apigee recommends that you store each certificate in a separate alias. |
| EDGEUI-1003 | Display full list of developers apps for CPS customers When viewing developer details, CPS customers are now able to view the full list of developer apps. In previous releases, the maximum number of developer apps that could be viewed was 100. |
Cloud 17.05.22 (API management)
| Issue ID | Description |
|---|---|
| MGMT-4059 | |
| MGMT-3517 | Incorrect proxy revision in proxy deployment error message |
Cloud 17.05.08 (UI)
| Issue ID | Description |
|---|---|
| EDGEUI-1041 |
Updating entities with extended ASCII characters fails due to improper
encoding |
| EDGEUI-1033 |
Edge UI Displays "Session Timed Out" for 403 Errors |
| EDGEUI-1019 |
Unknown error message displays when Edge UI times out |
Cloud 17.04.22 (API management)
| Issue ID | Description |
|---|---|
| MGMT-3977 | A security fix was made related to user permissions. |
Known Issues
This release has the following known issues:
| Issue ID | Description |
|---|---|
| 67169830 | NullPointerException in the response cache An object that was cached by a previous release may not be recovered from the cache correctly. |