You're viewing Apigee Edge documentation.
Go to the
Apigee X documentation. info
On Tuesday, April 21, 2015, we released a new cloud version of Apigee Edge.
If you have questions, contact Apigee Edge Support.
For a list of all Apigee Edge release notes, see Apigee Release Notes.
New features and enhancements
Following are the new features and enhancements in this release.
Server Name Indication (SNI) support
Edge supports the use of Server Name Indication southbound (from message processor to target endpoints). If you want to use SNI, contact Apigee Edge Support.
Java 1.7 is required.
With SNI, which is an extension of TLS/SSL, multiple HTTPS targets can be served off the same IP address and port without requiring all those targets to use the same certificate.
No Edge-specific configuration is required. If your environment is configured for southbound SNI (Edge cloud is by default), Edge supports it.
Edge automatically extracts the hostname from the request URL and adds it to the SSL handshake request. For example, if the target host is https://example.com/request/path, then Edge adds the server_name extension as shown below:
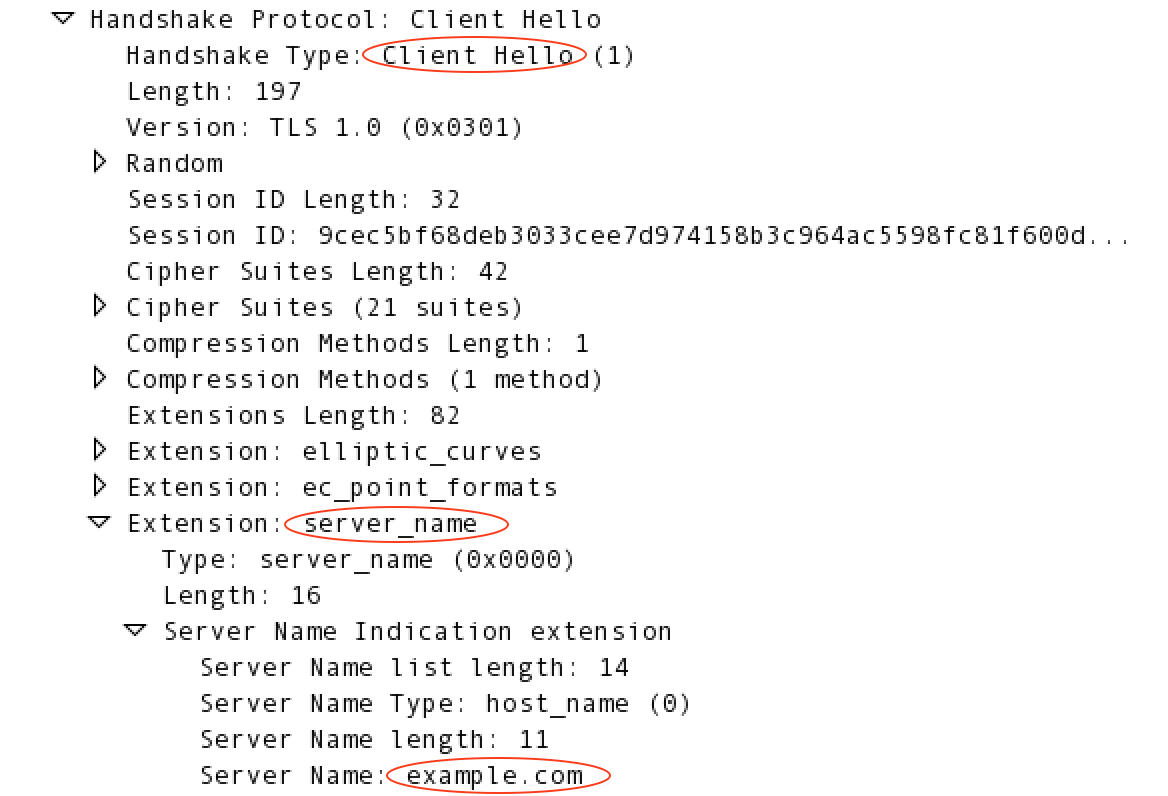
For more information on SNI, see http://en.wikipedia.org/wiki/Server_Name_Indication.
Apigee Community access from management UI Help menu
You can access the Apigee Community from the management UI Help menu.
Access Control policy
The Access Control policy has been enhanced to allow finer-grained evaluation of IP addresses
for allowlisting and denylisting when IP addresses are contained in the
X-FORWARDED-FOR HTTP header.
With multiple IP address checking enabled on the header (contact Support to set the
feature.enableMultipleXForwardCheckForACL), a new <ValidateBasedOn> element in
the policy lets you check against the first IP, the last IP, or all IPs in the header. For more
information, see Access
Control policy.
Management UI error messages
Error message display in the management UI has been redesigned.
New target variables in message flow
New variables in message flows provide more complete URL information for target endpoints and target servers:
- TargetEndpoint:
request.urlreplacestarget.basepath.with.query. - TargetServer:
loadbalancing.targetserverreplacestargetserver.name. Also,target.basepathis populated only when the<Path>element is used in the TargetEndpoint's HTTPTargetConnection<LoadBalancer>element.
"Signature Algorithm" in the SSL Certificates details
A new "Signature Algorithm" field has been added to SSL certificate details, viewable in the management UI (Admin > SSL Certificates) and the management API (Get Cert Details from a Keystore or Truststore). The field shows either "sha1WithRSAEncryption" or "sha256WithRSAEncryption", depending on the type of hashing algorithm used to generate the certificate.
Bugs fixed
The following bugs are fixed in this release.
| Issue ID | Description |
|---|---|
| MGMT-1899 | Resource paths deleted after saving product settings When editing an API product, the product's resource paths could get deleted if the user double-clicked the Save button. This issue has been fixed. |
| MGMT-1894 | Developer Apps page never finishes loading for the developer column |
| MGMT-1882 | New API proxy from WSDL only shows last parameter details |
| MGMT-1878 | If multiple revisions are deployed to an environment, Trace only shows one of them |
| MGMT-1872 | Not able to download Custom reports |
| MGMT-1863 | Node.js logs not viewable in management UI |
| MGMT-1825 | Cross-site scripting (XSS) bugs |
| MGMT-1804 | Node.js API is sending invalid JSON in some cases |
| MGMT-1799 | UI security vulnerability sending request in Trace |
| MGMT-1362 | Forgot Password email does not work if the Email address contains '_' |
| DEVRT-1514 | ObjectTransform breaks for some products |
| APIRT-1170 | Missing resource file caused MP fail to load an environment |
